According to a recent report, the tech giant Gigabyte suffered a data breach resulting from a ransomware attack, which compromised a large amount of confidential information protected by the company. According to PrivacySharks researchers, the exposed data was found on the onion platform of the AvosLocker ransomware group.
The leak was revealed a couple of days ago, when hackers posted an ad on their website claiming the information is legitimate and threaten to publish more information if the company refuses to negotiate the ransom. This group is characterized by selling the stolen information in its attacks, and this case is no exception; at the moment the amount of the ransom demanded is unknown.
The hackers posted a sample of the company’s extracted information in a 14 MB ZIP file. After a brief look at the leak, the researchers concluded that this sample includes data such as:
- Credit card numbers. The exposed cards date back to 2014, so it is almost a fact that they have already expired
- Passwords and usernames
- Payroll details
- Human Resources Reports
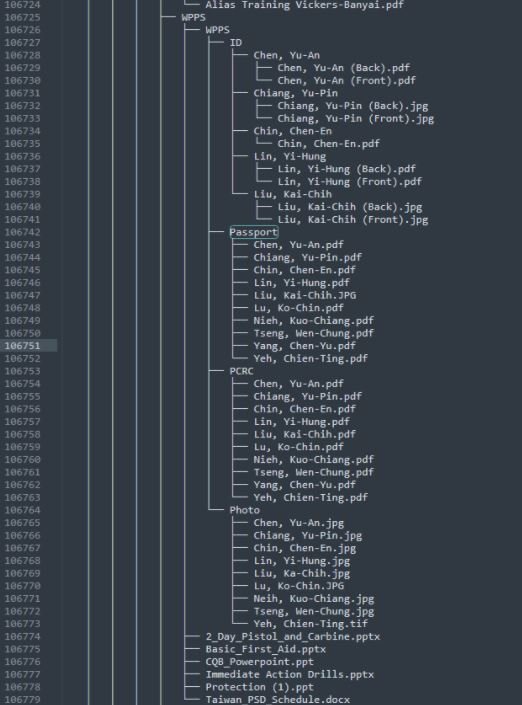
- 10 PDF documents in a file called “Passports”
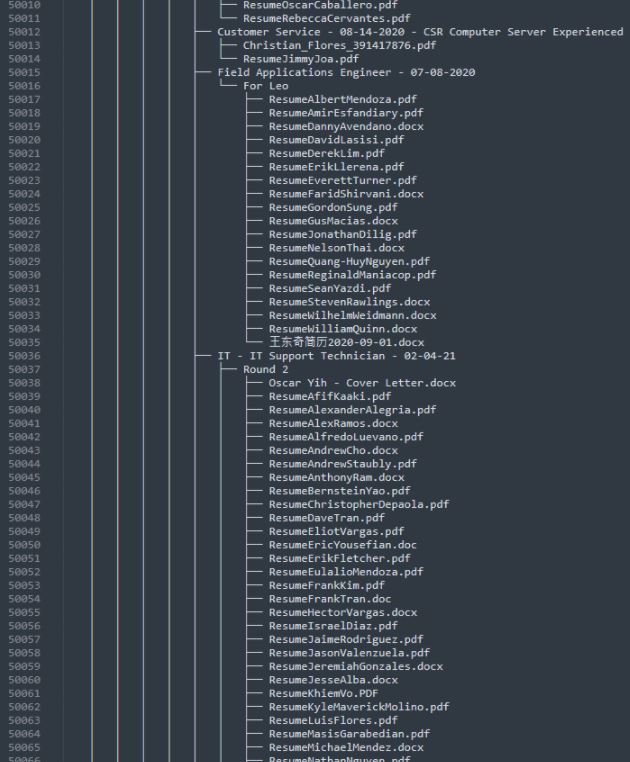
- Information on more than 1,500 job candidates, including full names, CVs and applications
- A zip file containing information from a deal with Barracuda Networks worth $100,000 USD
- Details of enterprise customers, including well-known companies such as Blizzard, Black Magic, Intel, Kingston, Amazon and BestBuy
While the details of the exposed cards date back more than five years, the confidential information of companies, employees and applicants seems to be completely up to date, so this leak represents a severe risk for these users.
These kinds of incidents are never good news for the companies affected and could reframe the way Gigabyte manages its IT security policies. At the moment, it would be in the company’s best endeness to try to protect employees and potential future hires against any security incidents stemming from the breach, as the nature of the compromised records would allow various hacking groups to launch ambitious attack campaigns.
Regarding negotiations with hackers, the U.S. government always recommends not making any payment and notifying the incident to the corresponding authorities, although at the moment it is unknown if Gigabyte decided to give in to the demands of the attackers or request the help of the police.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
