Zscaler’s team of researchers has detailed the finding of a new phishing campaign in which threat actors target large organizations around the world using Microsoft’s corporate image. This campaign stands out for targeting senior executives from affected organizations to steal administrator credentials and other sensitive details.
According to the researchers the potential victims receive emails with voice files attached. When trying to open these files, a fake Google reCAPTCHA screen will be launched to redirect users to a malicious website where cybercriminals will try to intercept sensitive information from victims. These phishing websites are hosted in generic domains such as .xyz, .club and .online.
The most prominent features of this campaign are described below, so that researchers can detect any indicators of engagement in their systems.
.XYZ DOMAINS
In phishing attacks with .xyz domains, malicious hackers send a targeted email from a unified communications system with an attached HTML file disguised as a voice mail message.
The following screenshot shows the contents of the HTML file with a phishing URL server <.>mvmail365office<.>xyz.
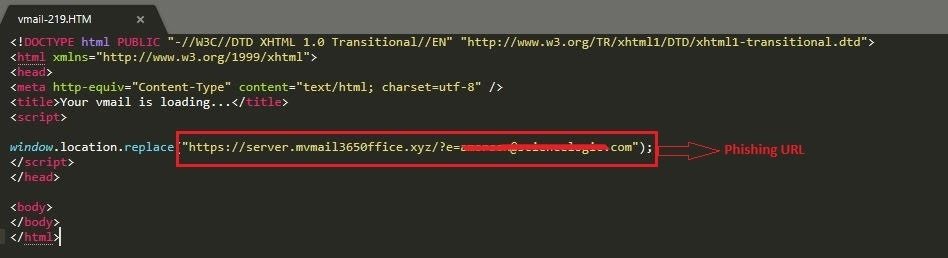
When the victim opens the attached HTML file, they are redirected to the aforementioned .xyz phishing domain.
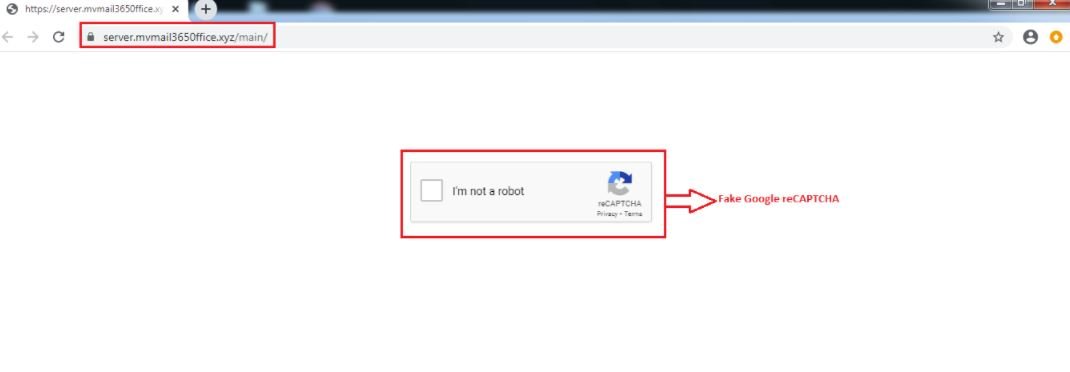
If this Google reCAPTCHA “verifies” the user, they will be redirected to Microsoft’s fake sign-in phishing page.
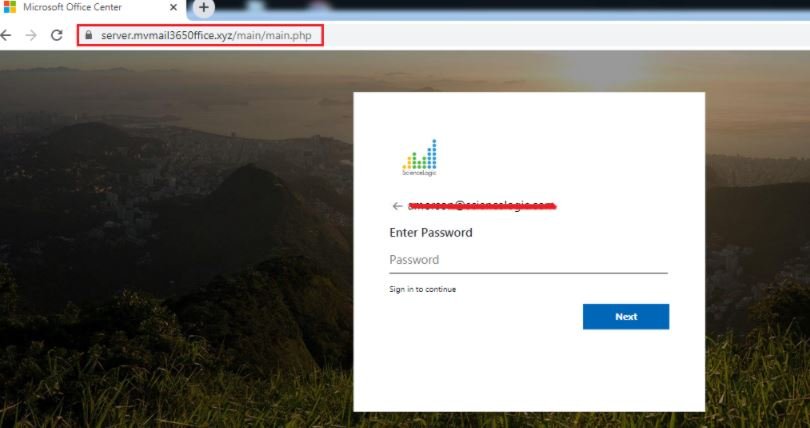
After submitting their login credentials, users will find the message “Successful validation”. Users are then shown a recording of a voice mail message that they can play, allowing threat actors to avoid suspicion.
.CLUB DOMAINS
Similar to the first campaign described, phishing attacks with .club domains begin when threat actors send spam with an html file attached, followed by a fake fake Google reCAPTCHA page, although this time it ends with hackers showing users a PDF file hosted on the malicious website.
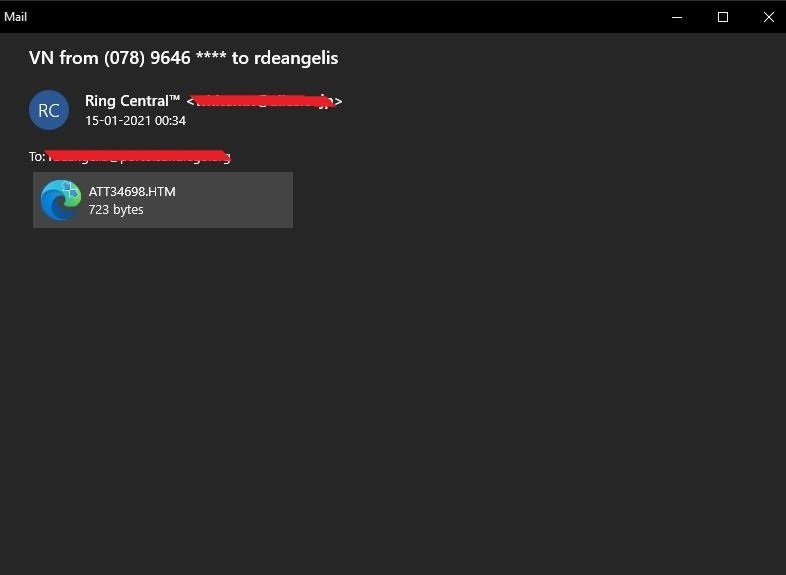
This image shows the obfuscated content of the attached HTML file.
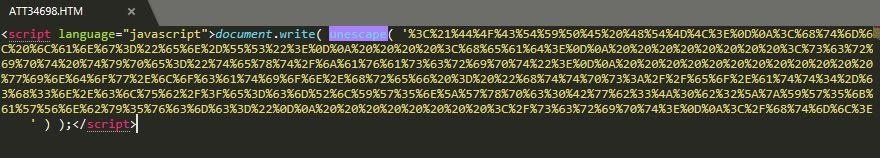
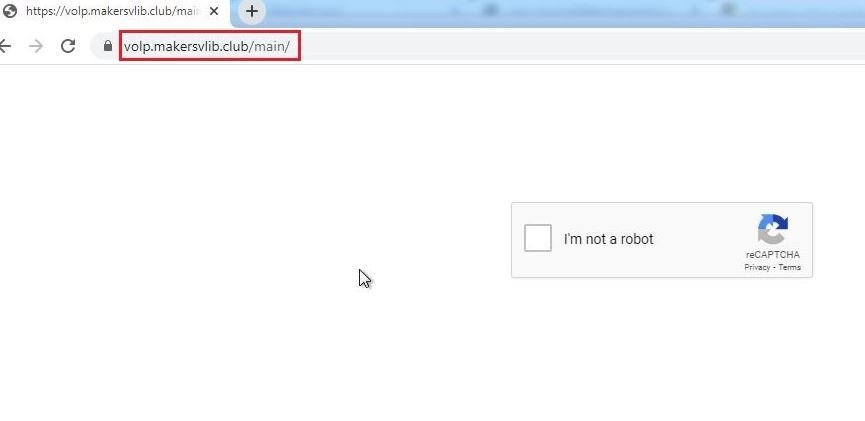
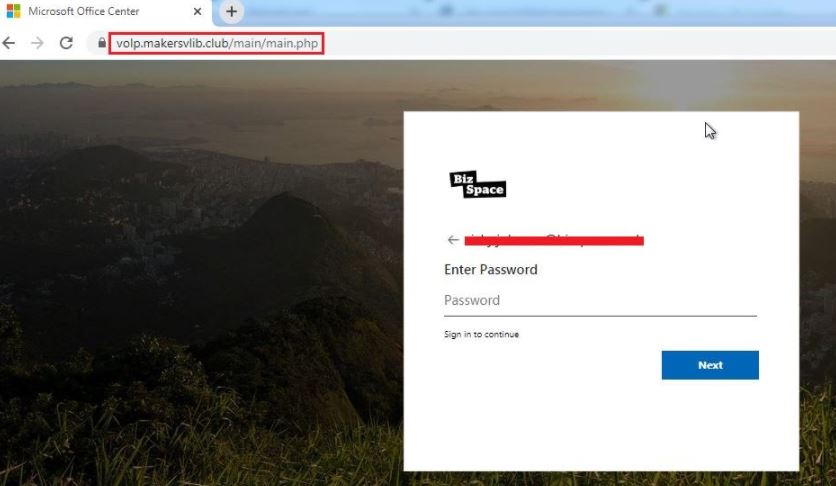
This phishing campaign is hosted using the volp<.>makersvlib<.>club domain with Google’s fake method reCAPTCHA.
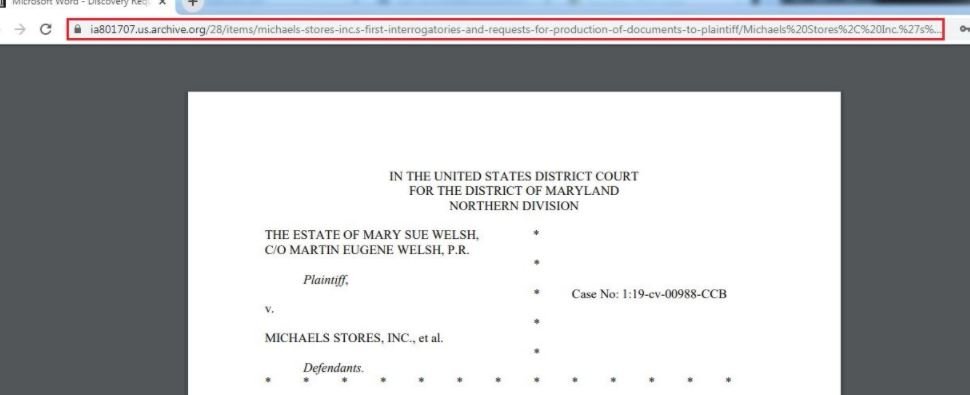
The above are screenshots of the phishing platforms used in this campaign.
.ONLINE DOMAINS
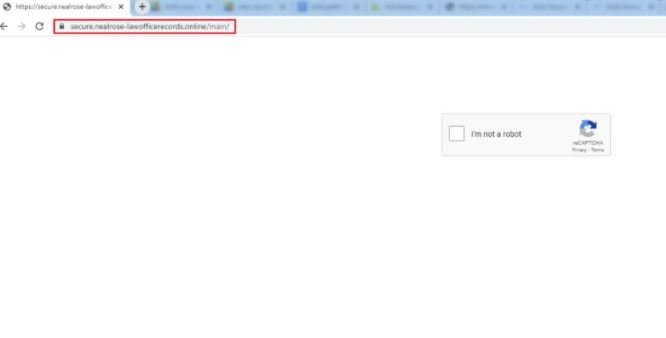
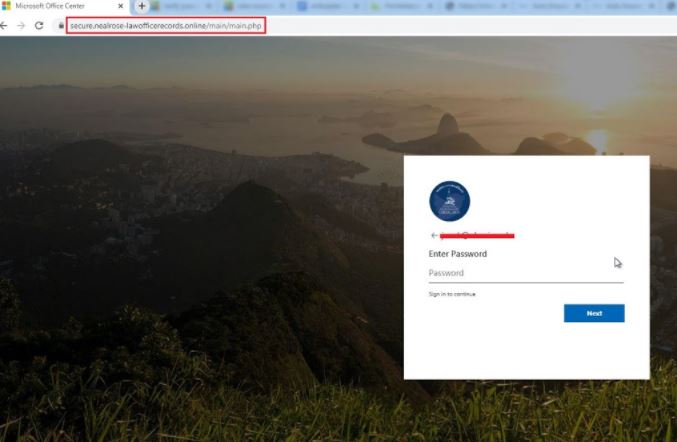
About the campaign in .online domains, researchers mention that in this case hackers send attached PDF files across the <.>nealrose-lawofficerecords<.> domain; when the user clicks on this file, they are redirected to a fake reCAPTCHA site and finally to a fake Microsoft login.
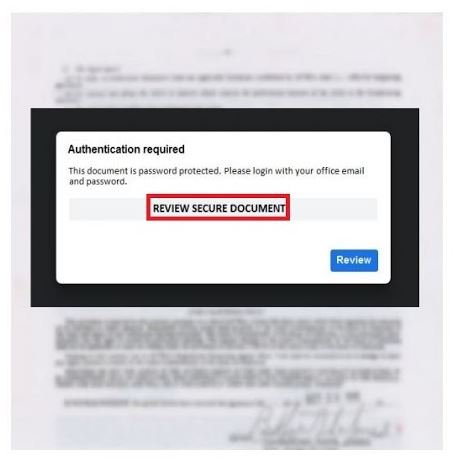
Generally speaking, all three campaigns operate in a similar way and share the same objectives, so experts should be aware of any indicator of engagement.
Experts claim to have blocked at least 2,500 phishing attempts related to this campaign in recent months, warning that the campaign remains active in at least 30 different domains.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.