Android is, along with iOS, the world’s most popular mobile operating system and has thousands of mobile apps to perform all kinds of tasks, making it a favorite target for the cybercriminal community. Faced with this situation, mobile app and device developers have had to familiarize themselves with the basics of mobile security, including penetration testing, scanning, and information gathering for indicators of compromise.
This time, the mobile security experts of the International Institute of Cyber Security (IICS) will show you the 10 best hacking tools for Android operating systems. Remember that this material was made for entirely teaching purposes and the information contained here in should not be misused.
It should be mentioned that these tools do not require a rooted device, so any user can become familiar with them. All tools work with the latest versions of Android.
WPS WiFi Checker Pro
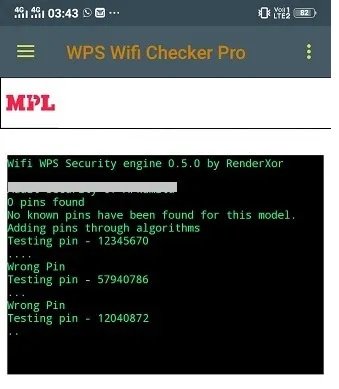
This application allows us to use the WPS mobile security protocol to analyze the protections of the router to which our devices are connected. After installation, WiFi Checker Pro initiates a LAN search to perform a PIN security and reliability analysis.
If the PIN is correct, the Android device will automatically connect to the vulnerable network, so the pentester does not need to know the WiFi password key. This tool allows you to spy on web activity on your network, making it an excellent tool for vulnerability analysis.
Kali NetHunter
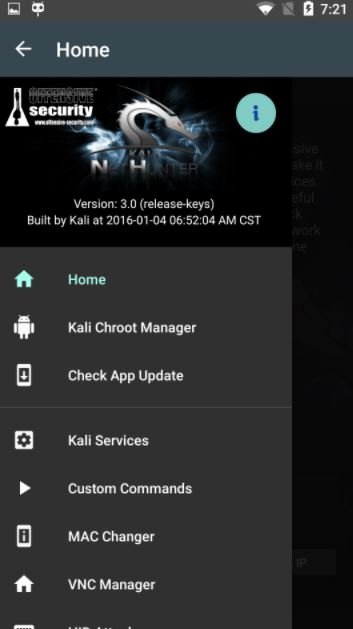
Offensive Security’s popular Kali NetHunter framework for hacking and pentesting is compatible with all kinds of Android devices, including manufacturers such as OnePlus, Samsung, LG and ZTE.
Kali NetHunter installs an operating system overlay on the target device, making it a resource-efficient pentesting tool. The tool can decrypt WEP and WPA keys, in addition to detecting open ports on other devices, mentioned by mobile security experts.
Mobile Pentesting zANTI
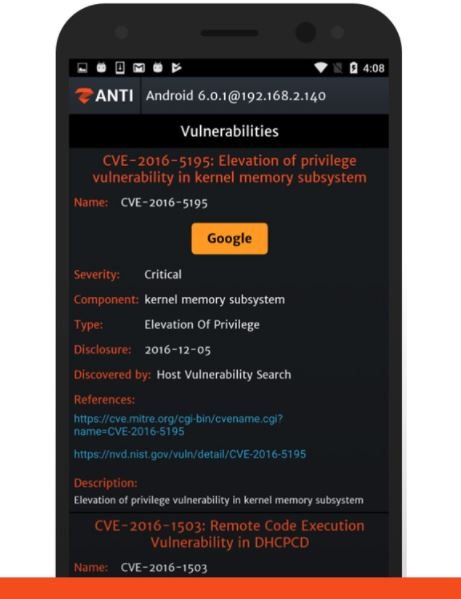
ZANTI is one of the most popular jailbreak apps for Android, allowing the identification and simulation of exploits and mobile hacking techniques.
This app collects a lot of information about connected devices, allowing you to analyze your mobile security and determine if a device is vulnerable to known attack variants.
Kayra the Pentester Lite
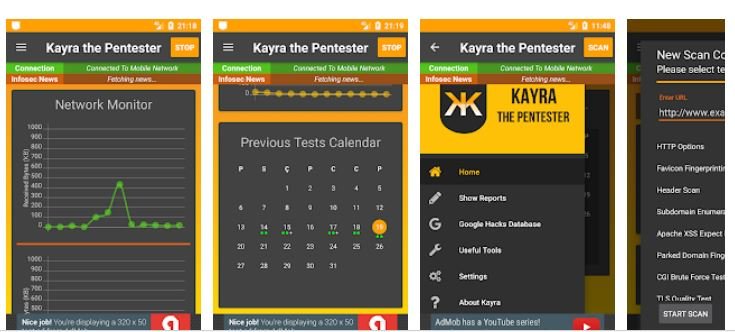
This is an open source app, free and available on the Play Store that has several metaploit frameworks integrated, which will allow the user to perform vulnerability tests through the analysis of various indicators of commitment.
Kayra can display the local network, perform header scans, initiate dictionary attacks, forge TCP packets, and even deploy Man-in-The-Middle (MiTM) attacks.
Hackode
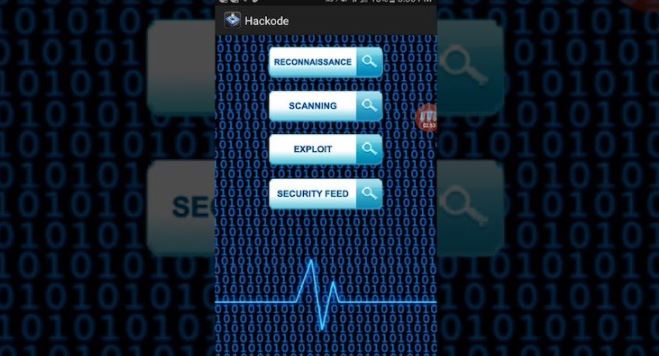
Hackode has multiple functions for collecting information about other devices.
In addition, mobile security experts can use the network tools built into Hackode, such as Google Hacking, Google Dorks, Reconnaisance, WHOIS search, TracerRoute, DNS Rig and others.
Network Mapper
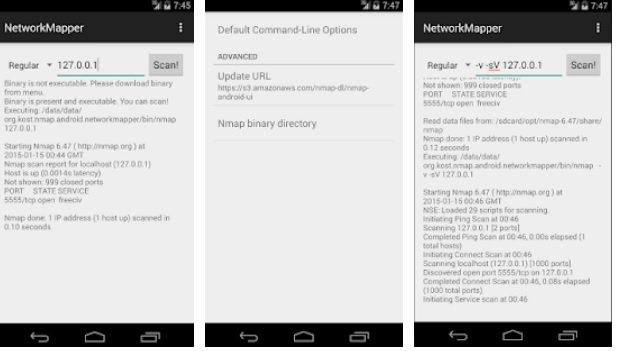
Network Mapper is a powerful tool based on the Nmap scanner to display and scan networks connected to a target device.
After installing the Network Mapper app from the Play Store, Nmap binaries will be automatically downloaded and installed, providing an easy-to-use graphical interface for scanning.
tPacketCapture
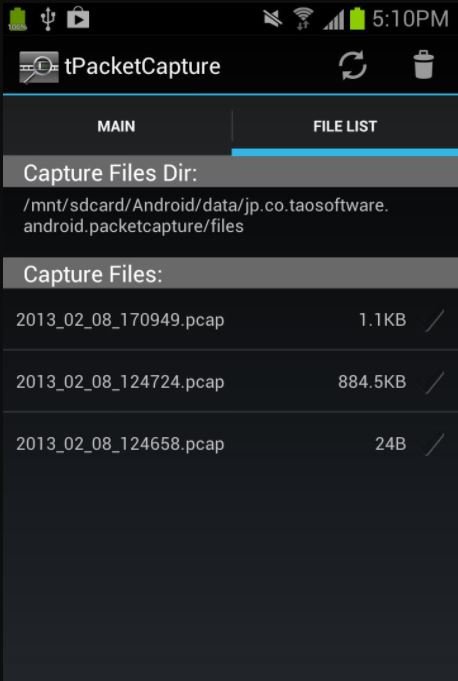
As its name suggests us, tPacketCapture is a mobile application for capturing packets and data transmitted over the target network.
Because tPacketCapture creates its own on-premises VPN, it works the same way on both rooted and non-rooted devices.
PortDroid
PortDroid is a complete network analysis package that contains many advanced features, providing a complete pentesting environment.
According to mobile security experts, the app perfectly fulfills all its functions, from pinging to port scans, DNS searches, among others, allowing administrators to be aware of everything that happens on their network.
WiFi Warden
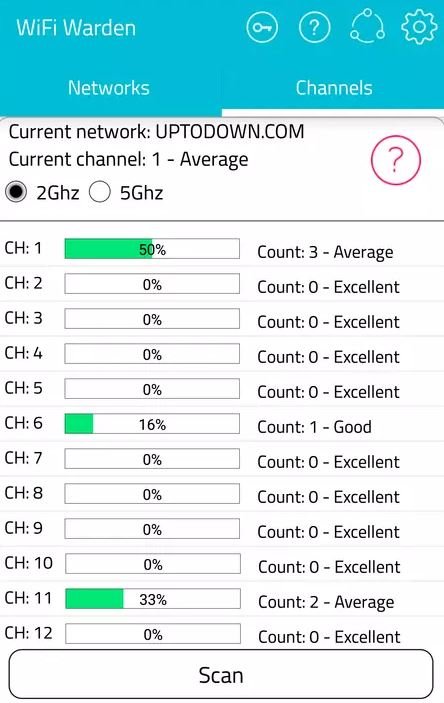
To use this tool, you have to give access to the location, since you can only hack the available networks within a certain radius.
To determine if the hacking has been successful, only one window will appear mentioning that the connection has been completed. Mobile security experts mention that this tool represents an ideal opportunity to use neighbors’ WiFi connection.
Termux
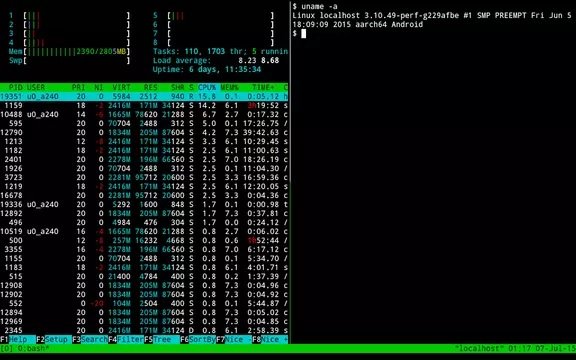
Termux is the real king of mobile hacking. This tool is capable of running any development for Kali Linux, from small scripts for simple tasks to complex tools like Metasploit.
This is a Linux terminal emulator for smartphones, which means that any Linux/Kali Linux command can be executed here and with a high degree of precision, so specialists won’t even notice the difference between using Thermux and a desktop computer.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
