Cybersecurity experts report the recent finding of a credit card skimmer capable of operating on all kinds of payment platforms, including Shopify, BigCommerce, Zencart and Woocommerce. Usually this kind of hacking tool is only compatible with a single platform due to differences in coding, demonstrating that developers have invested considerable resources for its creation.
This new skimmer displays a fake payment page to users of compromised websites, which features a keylogger to intercept all the information that users enter. This skimmer also throws an error after users press the “Continue” button in order to evade detection and redirect affected users to the legitimate payment process.
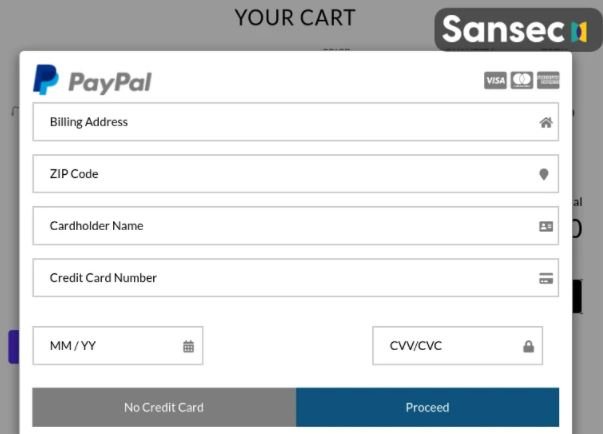
Experts mention that this is a remarkable attack technique: “Threat actors often focus on a single platform, so the range of this attack is much wider compared to previous campaigns,” says Sansec security firm report.
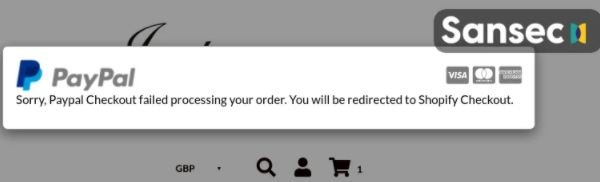
Due to the particularities of this campaign, experts have managed to identify skimmer related incidents, determining that attackers have been active at least since August: “Any website on which a user can enter a payment card could be affected,” the experts add.
Hacking groups have invested considerable efforts to develop new evasion methods. One of the methods that has caught the most attention of researchers is based on the use of a stealthy remote access Trojan (RAT) employed by the Magecart hacking group to generate persistence and avoid detection. These tools known as droppers have been detected on dozens of websites recently, mainly on trading platforms.
Experts continue to scan these platforms for new samples of malware and even new variants potentially present on payment platforms.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
