Cybersecurity specialists reported the detection of a critical vulnerability in the popular npm NETMASK library that could affect the more than 278,000 GitHub repositories that depend on this service. NETMASK is frequently used in hundreds of thousands of applications to analyze IPv4 addresses and CIDR blocks, and is downloaded by about 3 million users each week.
According to the report, the flaw present in the library implies that when parsing an IP address with a leading zero, NETMASK will instead identify a different IP due to the implementation of some erroneous validations. The flaw was reported by researchers Victor Viale, Sick Codes, Nick Sahler, Kelly Kaoudis and John Jackson.
The report mentions that the flaw, tracked as CVE-2021-28918, is related to how NETMASK handles mixed-format IP addresses, or more specifically when a decimal IPv4 address contains a leading zero.
It should be noted that an IP address can be represented in multiple formats, including hexadecimal and integers, although the most common IPv4 addresses are expressed in decimal format. As an example of this, BleepingComputer researchers note that their IPv4 address in decimal format is expressed as 104.20.59.209, which is equivalent in octal to 0150.0024.0073.0321.
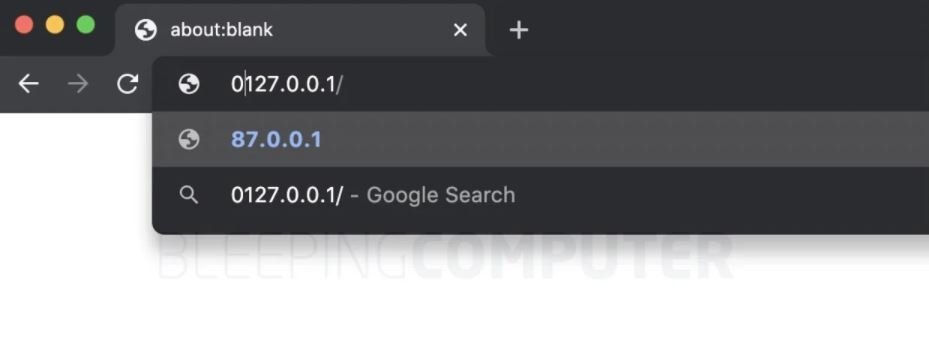
Suppose you receive an IP address in decimal format, 127.0.0.1, which is widely understood as the local or localhost loopback address. If you had to add a 0, should an application analyze 0127.0.0.1 as 127.0.0.1 or something else?
In the IP address for this example, in the case of the NETMASK npm library, leading zeros when converting to another format will be discarded. According to the original specification, parts of an IPv4 address can be interpreted as octal if they contain the prefix “0”; the problem is that NETMASK does not identify this, so it will always consider the parts as decimal and when attempting to validate an IP in a certain range, the representation of octal-based IPv4 addresses will be taken as incorrect.
This seems like a little error, although threat actors could influence the entry of the IP address analyzed by this application, creating the necessary conditions for the deployment of server-side request forgery (SSRF) attacks and even remote code execution.
“Think that someone is running a node server to disinfect an incoming request or query parameter that is expected to be a URI used for a later connection; Threat actors can create an IP with some or all of the base 8 octets and deploy SSRF attacks or even force a server to disconnect by changing the IP address format,” the experts add.
After receiving the report in a timely way, NETMASK developer Oliver Poitrey issued a set of security patches, as well as publishing some analysis cases to corroborate what is mentioned in the received report. The corrected version of NETMASK (v2.0.0) is now available, so users of affected versions are advised to update as soon as possible to prevent any attempt to exploit CVE-2021-28918.
To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
