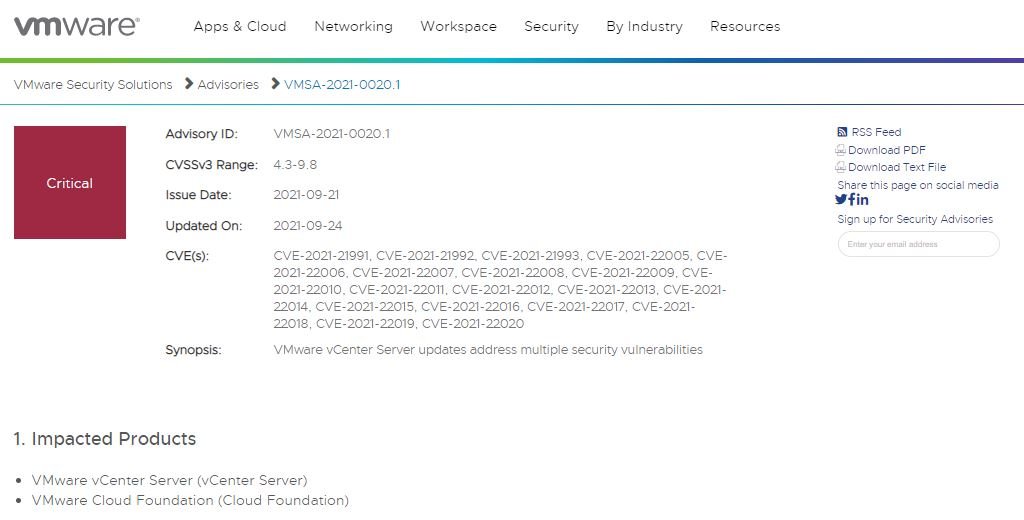
VMware security teams confirmed that the vulnerability in vCenter Server tracked as CVE-2021-22005 has already been exploited in the wild in a chained manner with other bugs fixed in the same update in which this flaw was addressed.
A few days ago the company notified its users that the updates released for vCenter Server addressed a total of 19 bugs, including the vulnerability described as an arbitrary file upload whose exploitation could lead to arbitrary code execution in the affected deployments.
Just hours later, security firm Bad Packets released a report noting the detection of limited activity related to CVE-2021-22005. Finally, a Vietnamese researcher identified as Jang published technical details and a proof of concept (PoC) exploit for this vulnerability.
Although as it is now the exploit cannot be used for attacks in real scenarios, the researchers mention that it can be used to attack vCenter servers. On the day the PoC exploit was released, Bad Packets reported that activity aimed at exploiting this flaw had increased markedly.
In response, VMware updated its security alert to confirm detection of exploitation attempts in the wild. The Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert to warn organizations about a possible mass exploitation campaign.
Separately, researchers at The Firm GreyNoise reported seeing attacks involving CVE-2021-22005 and CVE-2021-22017, another vCenter Server rhttpproxy bypass flaw. The two bugs were addressed in VMware’s latest update.
There are currently thousands of exposed vCenter servers on the Internet, although finding these flaws can also be useful for threat actors who gained prior access to the affected targets. A report from Censys points to the detection of at least 7,000 servers potentially compromised by the attacks described in this article, so it is critical that users of vulnerable deployments install security updates as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
