A report from security firm FingerprintJS details the detection of a critical bug in Safari web browser that would allow the leaking of sensitive users’ information including browsing history logs and linked Google accounts.
Apparently, the bug lies in Safari’s IndexedDB implementation on Mac and iOS, so a website can see the database names of any domain. Database names can be used to extract identifying information from a lookup table.
For example, Google services store an instance of IndexedDB for each of the user accounts initiated, with the database name corresponding to the Google user ID.
Exploiting these flaws would allow attackers to use a compromised website to extract a Google user ID and then use that ID to extract more personal information about the target user, as the ID is used to make API requests to Google services. A proof of concept (PoC) demonstrates how investigators managed to obtain a victim’s profile picture.
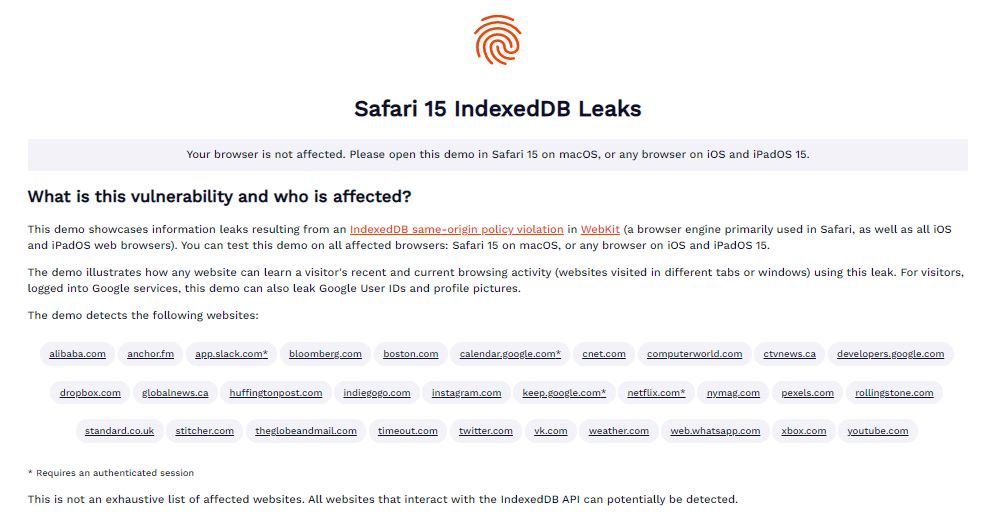
The demo only maintains a lookup table of approximately 30 domain names. However, the researchers believe there’s no reason the technique can’t be applied to a much larger set. Almost any website that uses IndexedDB’s JavaScript API could be vulnerable to this type of data extraction, experts add.
The error occurs because the names of all IndexedDB databases are available for any site, so the solution is that websites can only view databases created by the same domain name as yours. All current versions of Safari on iPhone, iPad and Mac are vulnerable to exploitation. FingerprintJS says the bug was notified to Apple on Nov. 28, though it hasn’t been fully addressed yet.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
