Cybersecurity specialists report the detection of a critical vulnerability in Vim, the improved version of the Vi text editor, present in all UNIX systems and developed by Bram Moolenaar in 1991. According to the report, the successful exploitation of this fault could put the affected systems at total risk.
Tracked as CVE-2022-1154, the flaw exists due to a use-after-free error within the utf_ptr2char() function in regexp_bt.c. This condition could be abused by remote threat actors to cause affected users to open specially crafted files and lead to an arbitrary code execution scenario.
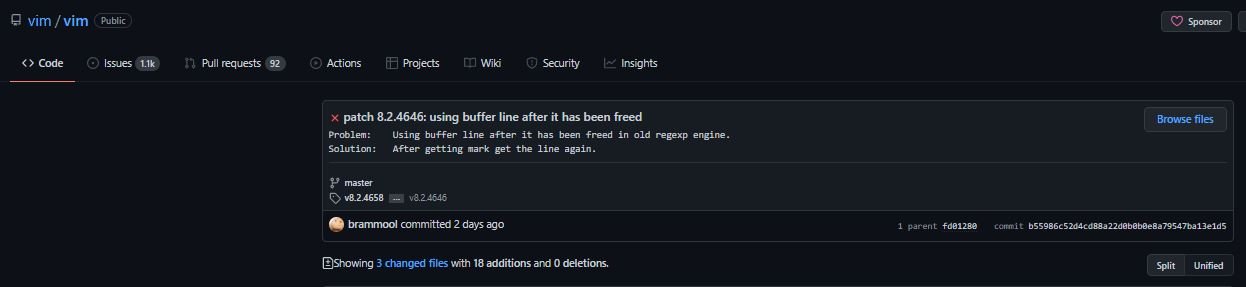
The flaw received a score of 7.7/10 under the Common Vulnerability Scoring System (CVSS) and is considered a high-severity bug because a successful attack could compromise fully exposed systems.
According to the report, the flaw resides in all versions of Vim between v8.2.0 and v8.2.4645.
A proof of concept (PoC) for the exploitation of this flaw is available online:
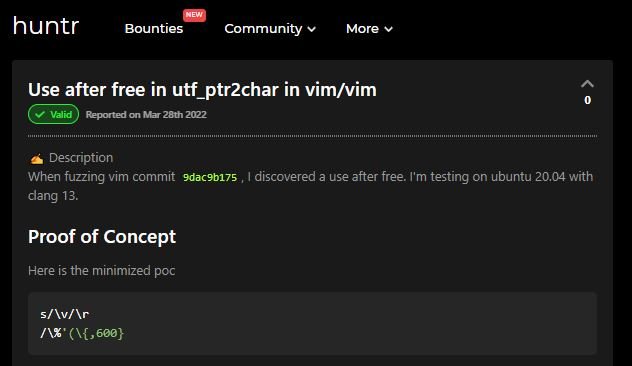
Although the flaw can be exploited remotely by unauthenticated threat actors, no active exploitation attempts have been identified so far. Still, Vim developers recommend users of affected deployments to update as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
