Cybersecurity specialists report the detection of a critical zero-day vulnerability in Argo Continuous Deployment (Argo CD), a widely used Kubernetes tool for automation of the deployment of desired application states to specified target environments. Hundreds of organizations use Argo CD for their automation tasks, including Alibaba Group, BMW Group, Deloitte, IBM, Intuit, Red Hat, Skyscanner and Swisscom.
Tracked as CVE-2022-24348, successful exploitation of the flaw would allow the theft of sensitive data from compromised implementations. The flaw received a 7.7/10 score according to the Common Vulnerability Scoring System (CVSS).
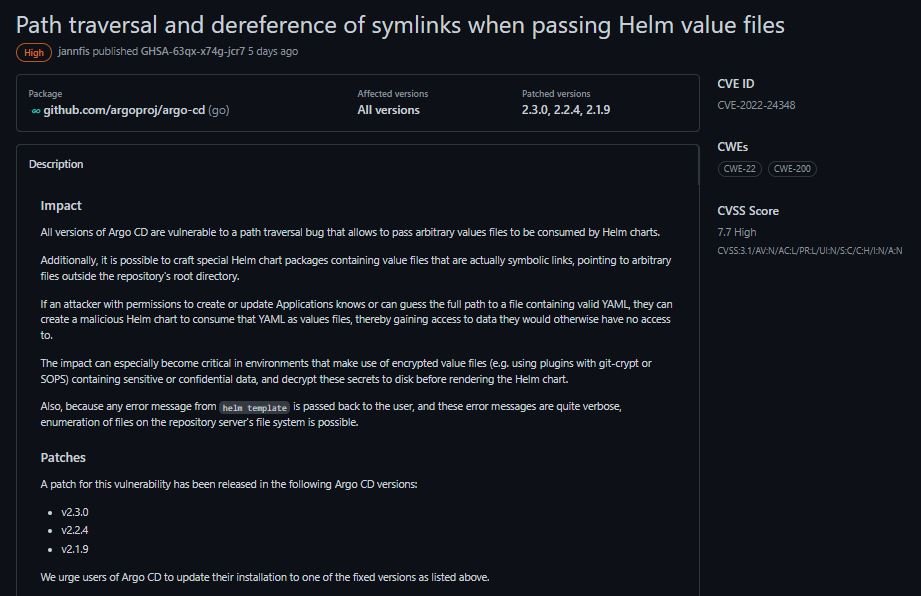
The vulnerability was described as a path-traversal error whose exploitation would allow threat actors to pass arbitrary value files, consuming Helm’s graphics: “Besides, it is possible to craft special Helm chart packages containing value files that are actually symbolic links, pointing to arbitrary files outside the repository’s root directory”, mentions the report.
Attackers can exploit the flaw by uploading a malicious Kubernetes Helm Chart YAML file, describing a set of Kubernetes resources used for deploying an application to the affected system, accessing sensitive information in other applications.
According to the report, threat actors can also use the information contained in the application files to make lateral movements: “Because application files generally contain a variety of transitive values of secrets, tokens, and environment-sensitive settings, malicious hackers can use this effectively to further expand their campaign by moving laterally through different services and performing a privilege escalation to gain more ground in the compromised system and resources.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
