The information security professionals at CyberCX have just revealed a means to routinely circumvent the protection of older Lenovo Laptops that have their BIOS locked, which raises serious concerns about users’ privacy and safety. Users are able to acquire unfettered access to the BIOS by following the instructions provided by one of the company’s executives, who expounded on a straightforward approach that involves connecting certain pins on an EEPROM (Electrically Erasable Programmable Read-Only Memory) chip using a standard screwdriver. After that, a quick examination of the screen displaying the BIOS settings was required in order to disable any BIOS password.
In addition, the BIOS password bypass demos that were carried out by CyberCX were carried out on many Lenovo laptops that were no longer being used in their intended capacity.
Because the EEPROM on these laptops is housed on a different chip from the core BIOS chip, it has come to light that the BIOS on these laptops is susceptible to a security breach.
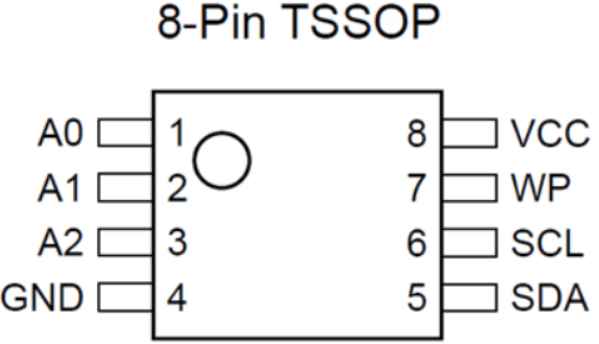
The EEPROM on the motherboards of Lenovo laptops is housed in a thin shrink small outline package (TSSOP) that has 8 pins.By carefully examining each chip that is located on the motherboard of the laptop, security experts are able to differentiate between different SOP, TSSOP, and TMSOP-8 packages.
While the EEPROM stores information and communicates with other devices via the Inter-Integrated Circuit (I2C or I2C) protocol.
The EEPROM on the motherboards of Lenovo laptops is housed in a thin shrink small outline package (TSSOP) that has 8 pins.

After searching up series numbers and checking chips on the mainboard that seemed to be potential candidates, it was ultimately possible to zero in on the appropriate EEPROM. It’s possible that this won’t always be the case, however the chip in the ThinkPad L440 has the marking L08-1 X on it.
The ‘hack’ described in the article includes an embedded video that demonstrates how simple it is to do the task. To complete the short between the L08-1 X chip pins, you need to do nothing more complicated than hold the tip of a screwdriver between two of the chip legs. Then, after you have entered the BIOS, you ought to discover that all of the configuration choices are free to be adjusted as needed. There may be some time requirements, but the timing requirements aren’t very stringent, so there is some wiggle room.
Because you cannot just short the EEPROM chips as soon as the machine is turned on (thus the requirement for time), CyberCX gives a rather in-depth study of how their BIOS hack works. This analysis illustrates why you can’t just turn the machine on and try to hack the BIOS.

There is a possibility that some readers have questions about their own laptops or BIOS-locked computers that they have seen on eBay or other online marketplaces. According to CyberCX, many newer computers that have the BIOS and EEPROM packages integrated into a single Surface Mount Device (SMD) would be more challenging to hack in this manner and would need a “off-chip attack.” The information security company also claims that several system builders and motherboard manufacturers currently employ an integrated SMD in their products. The security firm recommends that users who are more concerned about the safety of their data than about their computer’s operating system use “full disk encryption” to prevent an adversary from retrieving data from their laptop’s hard drive.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
