A recent report notes that video conferencing platforms are vulnerable to a new variant of cyberattack based on measuring LED light changes on audio output devices, allowing attackers to intercept and listen to sensitive information. The attack, dubbed Glowworm, could impact services like Zoom, Skype, Microsoft Teams and other popular platforms.
According to researchers at Ben-Gurion University, the technical term for this condition is “Telecommunications Electronics Material Protected from Emanating Spurious Transmissions” (TEMPEST) attack. This term is related to the emission of unintentional signals that can serve hackers to compromise an affected system. As a security measure, the U.S. Government requires federal agencies to protect their classified information from TEMPEST attacks.
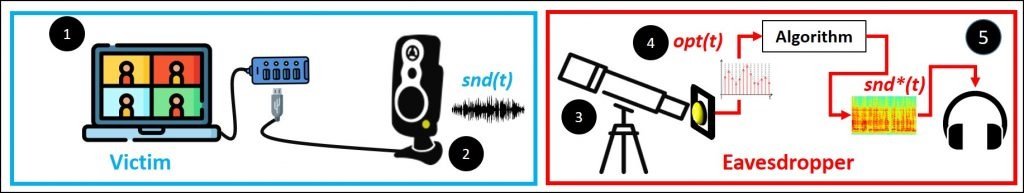
As mentioned above, the compromised information is obtained from the flicker of a device, be it a speaker, USB drive or LED power microcontrollers: “By analyzing the almost imperceptible changes in a device’s LED lights, the Glowworm attack can recover the audio of a videoconference session,” the report states. The researchers also mention that the vast majority of devices employed for videoconference sessions can be exposed to this attack variant.
In their report, the researchers showed that this attack is fully functional by extracting sensitive information from a computer’s speakers using a telescope equipped with an optical sensor at a distance of nearly 40 meters from the target. This sensor was directed to the LED indicator of the speakers, from where the researchers managed to extract clear fragments of a conversation.
Needless to say that this attack is highly complex and its deployment against a business or organization in the wild are almost unlikely; nonetheless, this is a good reminder that video conferencing platforms are riddled with vulnerabilities, so their secure use is not guaranteed by developers. Government agencies should be especially attentive to such reports, mainly because it is a requirement set by the federal government.
A detailed report of these findings is available on Ben-Gurion’s official researchers’ platforms.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
