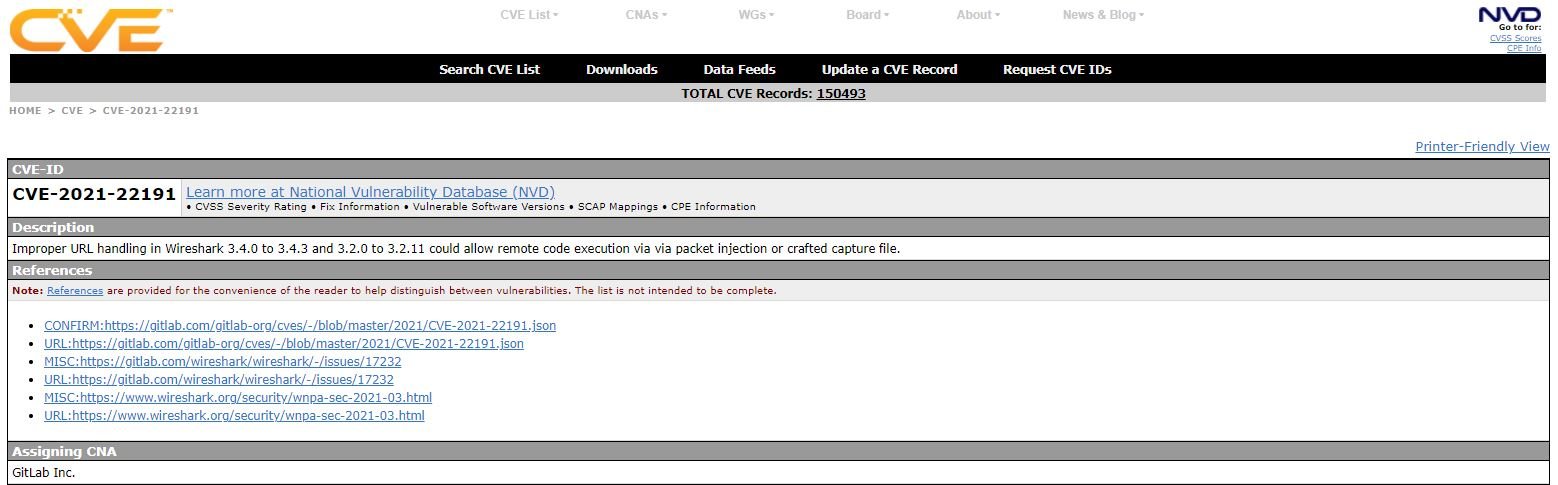
Cybersecurity researchers report that it is possible to use specially crafted Wireshark packages to deliver malware under certain conditions, especially when a target user double-clicks the URL fields of a given file. Other variants of this attack would allow other users of this tool to be compromised, widely used by computer security and pentesting experts of operating systems such as Windows or some Linux distributions.
This attack was reported by cybersecurity specialist Lukas Euler, who expressly requested the issuance of a CVE tracked key for security issues related to this attack. It should be noted that a CVE key is not normally assigned to faults detected in Wireshark, although in this case the developers made an exception and granted this flaw the tracking key CVE-2021-22191, which has already been fixed by an update.
In this regard, a group of researchers mentioned that this problem could be related to some changes made in Wireshark about 17 years ago. Experts mention that this problem exists because referenced files will be opened by the standard system application associated with a specific file type; Euler mentions:
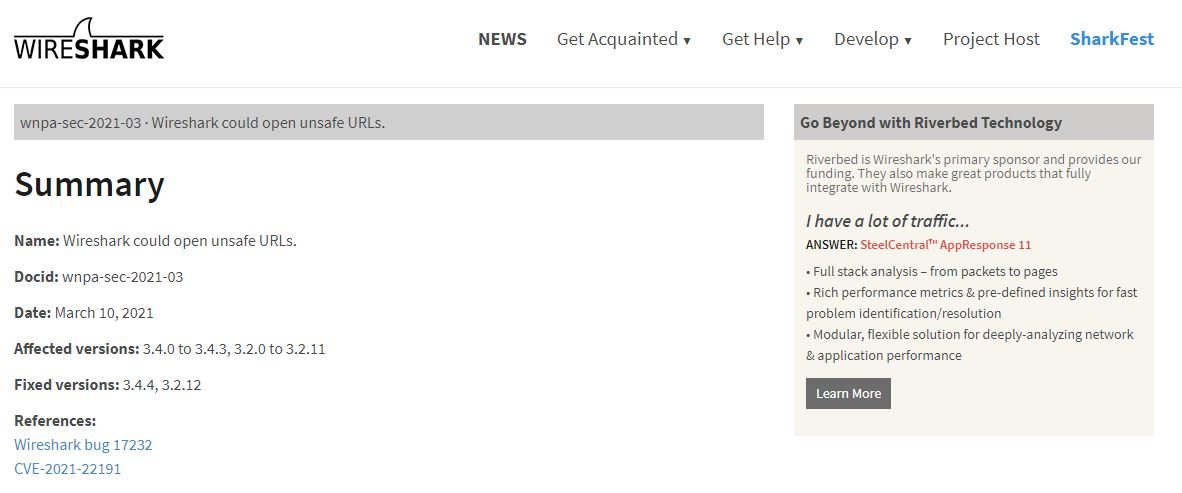
“In some fields of proto_tree Wireshark file you can double-click and pass URLs with arbitrary schemas to the QDesktopServices::openUrl function; the http and https URLs passed to this feature are opened by the browser, which is generally secure. Moreover, for some other schemas such as dav and file, referenced files will be opened by the standard system application associated with their file type. By preparing shared and executable files hosted on the Internet, arbitrary code execution can be achieved through malicious pcap (ng) files or captured live traffic and some user interaction.”
On Windows machines, if a user opens the malicious pcap file and double-clicks the file URL, the WebDAV share is mounted in the background and the .jar. A similar attack is possible in Wireshark for Xubuntu, but with an NFS share and a malicious .desktop file.
In this regard, Wireshark recommended that its users upgrade to the latest available versions (3.4.4 or 3.2.12), which contain the corresponding updates: “The issue in GitLab also links the relevant merge requests; the code difference shows that the computer chose to fix the problem by copying the malicious URLs instead of opening them directly,” Euler says.
To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
