Cybersecurity specialists reported the detection of a new cyberattack method that would allow threat actors to deliver phishing emails inadvertently for security mechanisms, exploiting a key difference in the way inboxes and browsers read a URL.
According to the report, presented by security firm Perception Point, malicious hackers should only create a link using the “@” symbol in the middle; while email security filters will interpret this symbol as a comment, for web browsers, this indicates a legitimate web domain. Consequently, emails arrive seamlessly in the inbox and, if a user clicks on these links, they are redirected to a fraudulent website.
A few days ago, researchers detected a potential phishing email whose creators were trying to disguise it as a Microsoft message.
This message included a link to a supposed login page for Outlook. The authors of this campaign did sloppy work, employing bad designs, and using the domain name “storageapi.fleek.co”, followed by multiple random characters.
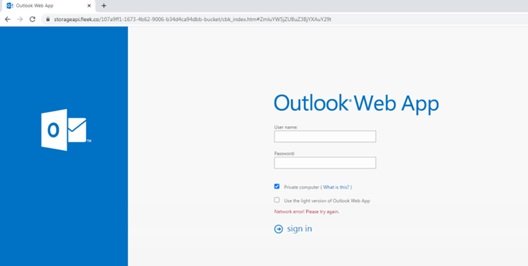
The message was clearly an attempted attack, so it seemed inexplicable that hackers could have bypassed email security filters. Soon after, the researchers discovered that the key is in the links attached to the email.
The URL embedded in the phishing emails detected by the researchers is:
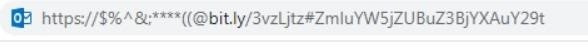
As mentioned above, browsers will read this as a URL, although email services interpret this symbol differently: “Email security systems will ignore a ‘@’ sign when used within the message text, and there are many cases of legitimate use,” reports Perception Point.
Nonetheless, in these cases the symbol “@” works as a cover to hide the malicious link.
The hackers behind this campaign did a terrible job, so the researchers discovered an IP associated with the campaign, discovering that this activity originated in Japan. Apparently, their targets include telecommunications companies, web services, and financial institutions.
For researchers, it’s fortunate that hackers have been so careless, as this ingenious method of hiding links to malicious websites could have proved devastating in the hands of an advanced hacker.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
