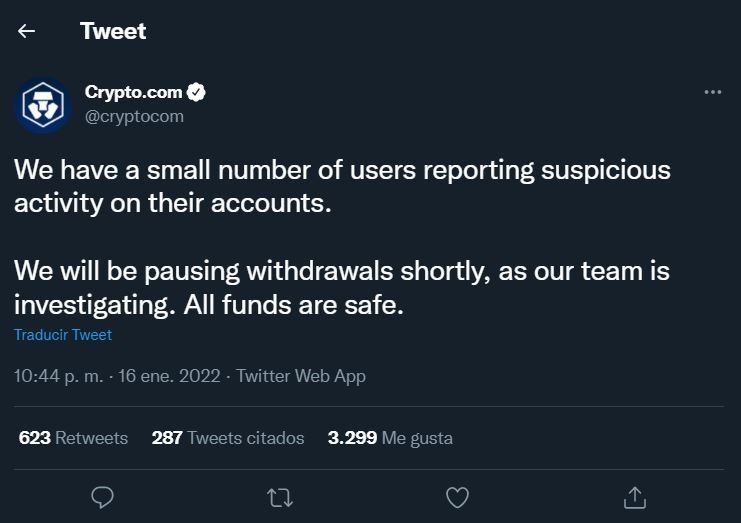
In a statement released this morning, Singapore-based cryptocurrency exchange platform Crypto.com confirmed that a “small number of users” were targeted for unauthorized activity on its systems. While the company did not confirm the number of affected users, the message ensures that all users’ assets are safe.
Threat actors appeared to gain access to the accounts of affected users regardless of whether they had two-factor authentication (2FA) or biometric identification enabled.
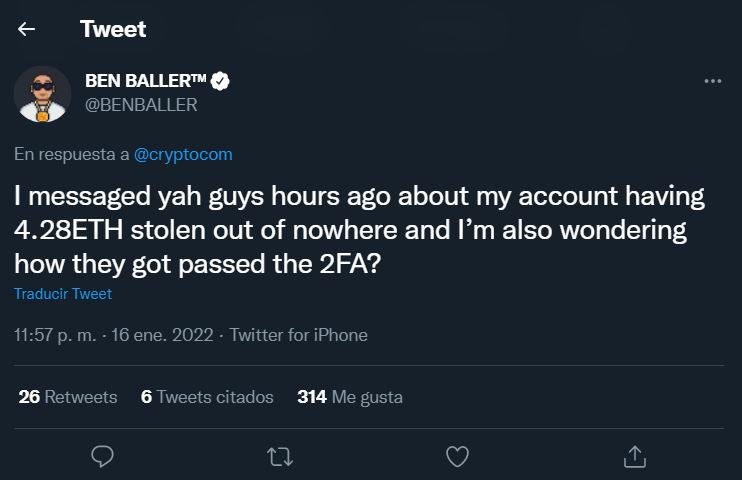
Reports about this potential hacking began to circulate for hours through platforms such as Twitter, where some users claimed that their accounts on Crypto.com had been compromised. Ben Baller, actor and user of Crypto.com, reported to the platform alleged indications of suspicious activity that resulted in the loss of $13,700 USD.
Another user identified as @NickDushko tweeted that his online Crypto.com wallet was hacked by an unknown actor who went on to make 7 Bitcoin transactions, equivalent to $11,000 USD.
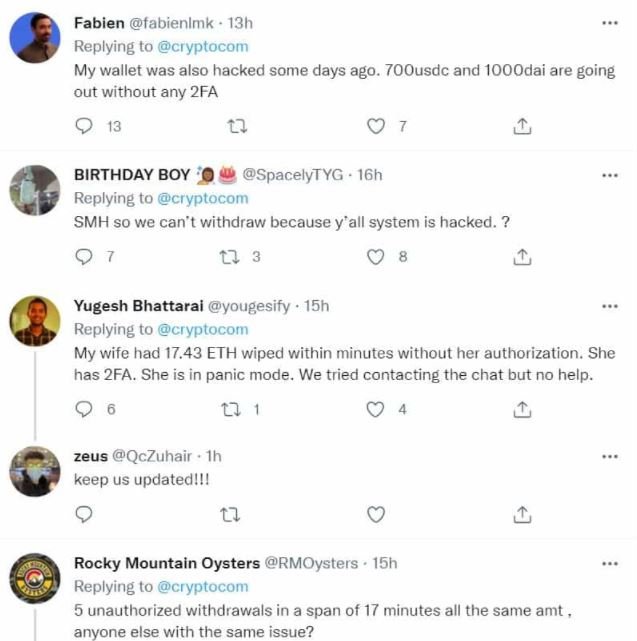
These complaints were shared by dozens of users on the platform.
A couple of hours ago, Crypto.com finally announced that some measures would begin to be implemented, including the temporary interruption of any transactions and the initiation of a thorough investigation. Kris Marszalek, CEO of the platform, assures that all funds are safe, although some additional security measures will be implemented, including the forced enablement of multi-factor update for all active users.
Although this incident has taken Crypto.com users by surprise, it is certainly anticipated by cybersecurity specialists, who have seen an increase in cyberattacks against cryptocurrency exchange platforms around the world. While in its latest update Crypto.com announced that transactions will be reinstated shortly, no further details were added about the causes of the incident, the losses generated and the possible consequences of the attack on other platforms.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
