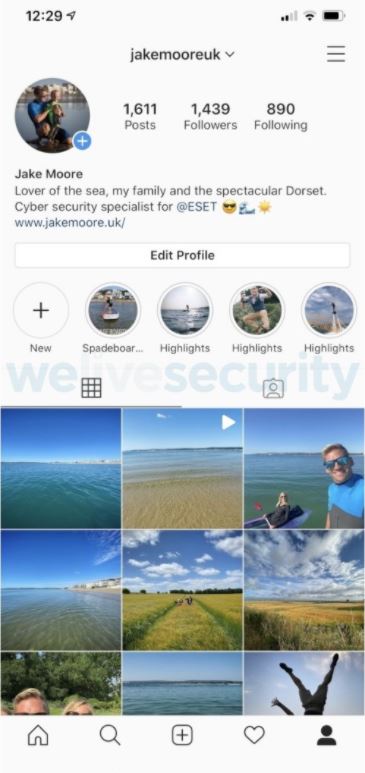
A recent trend of digital fraud is the cloning of accounts, in which criminals create social media accounts, mainly Instagram, using screenshots of the target account to try to trick other users into believing that their original account was compromised in order to obtain bank transfers.
To demonstrate the ease with which a fraud like this can be carried out, Jake Moore, security expert form ESET, cloned his own Instagram account and contacted some of his followers, who didn’t even imagine it was all about a cybersecurity experiment.
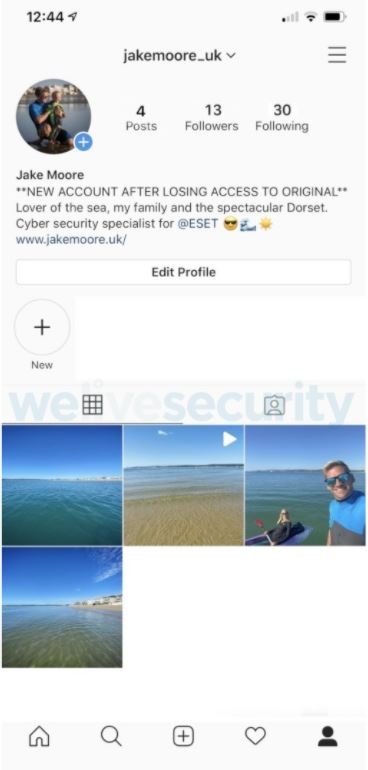
Taking screenshots of his own account, Moore created a new profile with the same images used in the original profile, adding to his bio the phrase: “NEW ACCOUNT AFTER LOSING ACCESS TO THE ORIGINAL”.
Once the account was cloned, Moore began following 30 of his followers on the original account; shortly after the cloned account I already had some followers: “I expected one of my friends to contact me by phone or any other means to verify that this new account really belonged to me,” the researcher says.
Contrary to what Moore expected, no one questioned the authenticity of the account; even more of his friends began to follow the cloned account. Taking the experiment to its next stage, Moore began sending Direct Messages (DM) to his followers on the cloned account, mentioning that a security incident had compromised his previous account, so he had decided to create a new one.
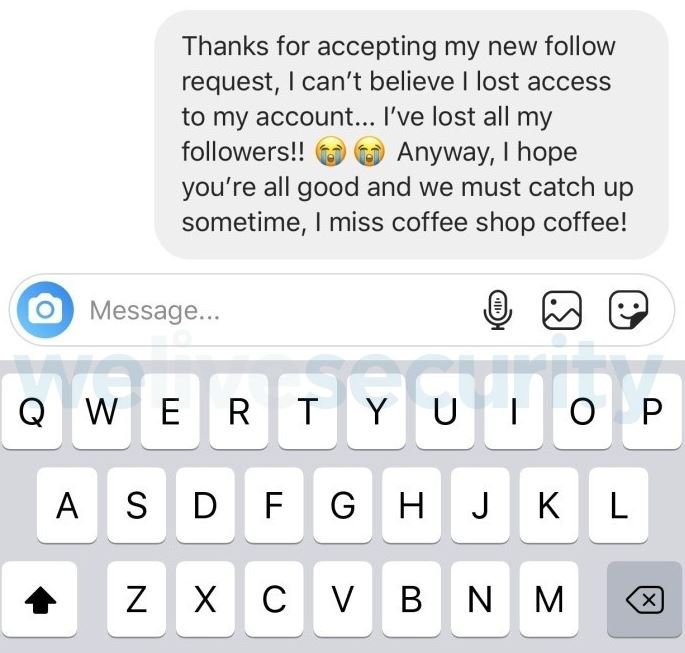
Moore sent this message to 13 of his followers, 8 of whom responded shortly.
To continue, Moore began interacting with the accounts that had responded to his message, trying to establish a credible and coherent story before carrying out the final step of the attack: asking his followers for an electronic transfer through a PayPal account. This is a basic method in social engineering campaigns carried out by hacker groups.
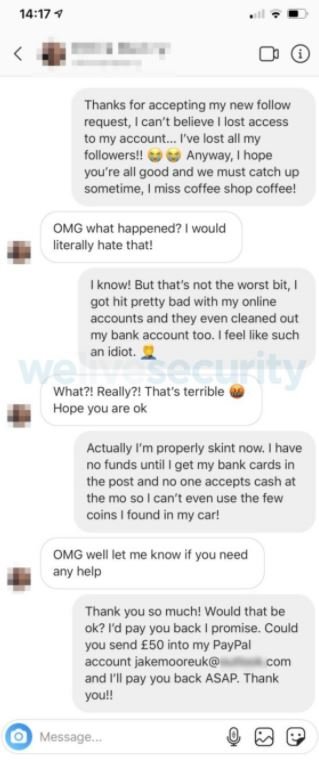
In some of the cases, the researcher’s followers even offered him help without Moore even mentioning it.
Threat actors depend on users creating the scam, so it is best to try to verify the identity of the owner of an account cloned by WhatsApp, Facebook, Twitter or any other means. However, the best way to prevent these incidents from occurring is by limiting the amount of personal information available on our social media profiles, as this is what allows threat actors to create fake profiles in order to deceive users.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.