After an investigation by the non-governmental organization Brennan Center for Justice, it was discovered that a couple of years ago the Los Angeles Police Department (LAPD) hired the services of Voyager Labs, an information collection firm that claims to have the necessary technology to identify possible crimes before they are committed.
At first glance, Voyager Labs looks like any other data collection and analysis firm; however, it is enough to read the documents obtained by the NGO to realize that the services of this company go far beyond the search for information in public sources, such as social media platforms.
According to the Brennan Center for Justice, Voyager says that its software is able to identify suspects through their online accounts to identify their close contacts, acquaintances and potential accomplices, using artificial intelligence to find motivations to commit a crime, either for economic, emotional and even ideological reasons. In addition, Voyager hinted that the LAPD could perform monitoring maneuvers using fake accounts from social platforms such as Facebook, Instagram and Twitter.
The investigation also notes that LAPD and Voyager ended a pilot test period in November 2019, after which authorities decided to continue using this technology for at least another year, though talks are said to be ongoing. An LAPD spokesman said the department is not currently using Voyager, though he declined to answer further questions.
While the LAPD has been recognizing social media as a vital source of information in the investigation of some criminal cases for years, cybersecurity experts have been seriously concerned about the use of software such as that provided by Voyager Labs, since the line between its legitimate use and the violation of the civil liberties of U.S. citizens is really blurred, which law enforcement agencies intentionally take advantage of.
The cybersecurity community began to notice this practice when reports began to pile up about laPD ordering its officers to collect information on seemingly random civilians, questioning them without a warrant in something known as “predictive policing.”
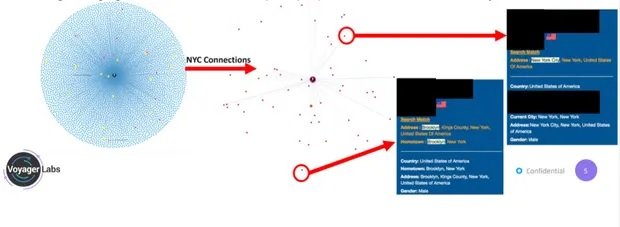
About the Voyager tools to which LAPD had access, the NGO failed to determine the specific name of each software sample or if any of these tools allowed obtaining evidence presented in a trial, although they assure that the Department investigated around 500 profiles on social networks, in addition to analyzing thousands of private messages. In addition, an anonymous LAPD investigator mentioned that Voyager’s software made it possible to “investigate in detail some targets, including some gangs.”
At the beginning of 2020, LAPD and Voyager were negotiating a possible contract extension, for which the company sent multiple documents to show how its most advanced tools worked. In this demonstration, Voyager detailed how its software made it possible to investigate a New York-based pro-Muslim activist, who was allegedly hatching a plan to intentionally spread a COVID sample among various Egyptian government officials.
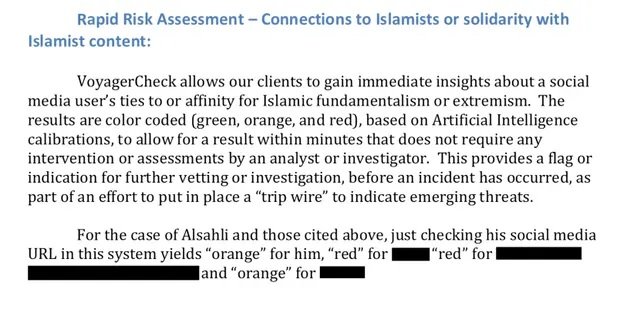
The company claimed that this investigation was carried out by federal agents, although it did not provide further information about the results of the operation. Voyager concluded by mentioning that this software was able to analyze thousands of posts on the social networks of the activist investigated, work that extended to more than 4,000 of his contacts on social networks.
As mentioned above, this company’s practices have caught the attention of the cybersecurity community and civil liberties activists. Rachel Levinson-Waldman of the Brennan Center for Justice believes that a key factor in the company’s conduct is the complacency of the authorities, who not only allow Voyager to spy on citizens but even collaborate with them.
Another factor that worries experts is that Voyager Labs seems to be a large company without a name, since it does not even publish its services on a publicly accessible platform, but offers its customers a first access to some information collection tools and then offers its most sophisticated developments, which indicates that its managers feel more comfortable without people in general knowing exactly what does this company do.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
