Right now we have accounts in all services in the world. Yes on Amazon, yes Netflix, yes on the PlayStation Store… but we can’t forget that we also have a bank account and Social Security.
How many times have we told you that you have to put secure, long and complicated passwords in each service in which we register. It seems silly, but we are all susceptible to being hacked. Even if you are not a well-known character, hackers no longer discriminate.
Well, what would you tell us if we told you that there is a new hacking tool that can circumvent all our security and steal our logins from all the services to which we are subscribed? Well, go preparing the answer because it is a reality.
A new hacking tool can supposedly bypass all established security protections to prevent cyber-attacks and gain access to any website.
The operator behind the tool, called EvilProxy, says it is capable of stealing authentication tokens needed to bypass multi-factor authentication (MFA) systems used by companies like Apple, Google, Facebook, Microsoft, and Twitter.
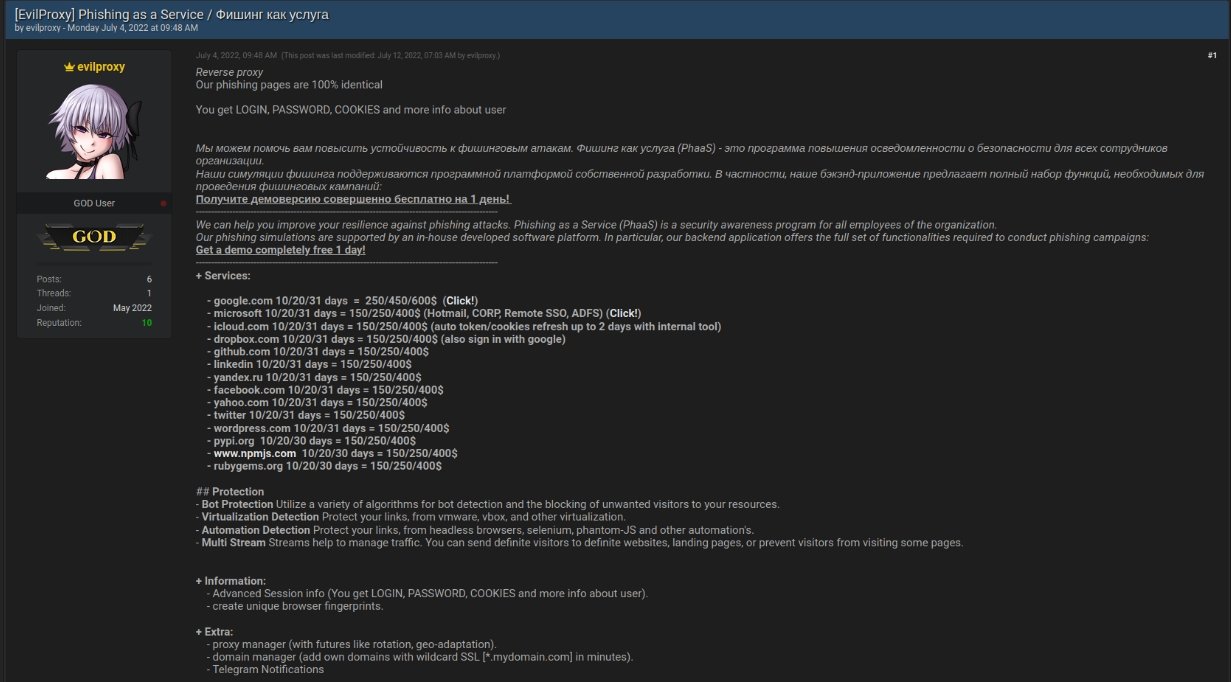
The service is especially worrying, as it promises to make these types of attacks available to all hackers, even those who don’t have the necessary skills or knowledge to attack such difficult targets.
The tool was discovered by security firm Resecurity, which notes that EvilProxy (also known as Moloch) is a phishing platform as a reverse proxy service. advertised on the dark web.
It offers theft of usernames, passwords, and session cookies for $150 for ten days, $250 for 20 days, or $400 for a month-long campaign, though attacks against Google cost more, $250, 450 and 600 dollars respectively.
Reverse proxies typically sit between a website and some kind of online authentication endpoint, such as a login page. EvilProxy tricks its victims using phishing lures, taking them to a legitimate page where they are asked to enter login credentials and MFA information.
This data is sent to the intended legitimate website, initiating the session, and also generating a session cookie containing an authentication token, which is sent to the user.
However, this cookie and authentication token can be stolen by the reverse proxy, which, as noted, sits between the user and the legitimate website.
Attackers can then use this token to log in to the site by posing as their victim, obviating the need to re-enter information in the MFA process.
Resecurity notes that aside from the cunning of the attack itself, which is easier to deploy than other man-in-the-middle (MITM) attacks, what also sets EvilProxy apart is its ease of use.
Upon purchase, customers receive detailed instructional videos and tutorials on how to use the tool, which features a clear and open graphical interface where users can set up and manage their phishing campaigns.
It also offers a library of existing cloned phishing pages for popular Internet services, which along with the names mentioned above, include GitHub, Dropbox, Instagram, or Yahoo.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
