Researchers from the security company Eclypsium investigated the AMI firmware that was stolen in the 2021 ransomware attack. They discovered vulnerabilities that had been dormant for years. They are vulnerable to exploitation by any local or remote attacker who has access to an industry-standard remote management interface called Redfish. This allows the exploiter to execute malicious code that will run on every server inside a data center. In December of 2022, Eclypsium revealed other faults that were uncovered throughout the course of the same study endeavor. The emphasis of the investigation was on the data that was compromised as a consequence of the ransomware attack that had been carried out in 2021 against the motherboard manufacturer Gigabyte, which was also a partner in AMI’s supply chain. BMC&C is an abbreviation that stands for “background monitoring and control,” and it refers to the vulnerabilities that were found by the cybersecurity company in the AMI BMC. The BMC software gives administrators the ability to remotely monitor and operate a device, eliminating the need to navigate the device’s operating system or the apps that are already installed on it. It is also possible to use it to install operating systems, perform firmware updates, and examine logs. In spite of the fact that these capabilities render BMC very helpful, they also make it an alluring target for malicious actors.
The Baseboard Management Controller (BMC) that was manufactured by AMI may be found in millions of devices across the globe since it is integrated into the goods produced by major corporations such Ampere, Asrock, Asus, Arm, Dell, Gigabyte, HPE, Huawei, Inspur, Lenovo, Nvidia, Qualcomm, Quanta, and Tyan.
Eclypsium announced two new vulnerabilities: CVE-2023-34329, a major authentication bypass problem that can be exploited by spoofing HTTP headers, and CVE-2023-34330, a code injection flaws. Both vulnerabilities may be exploited by spoofing HTTP headers.
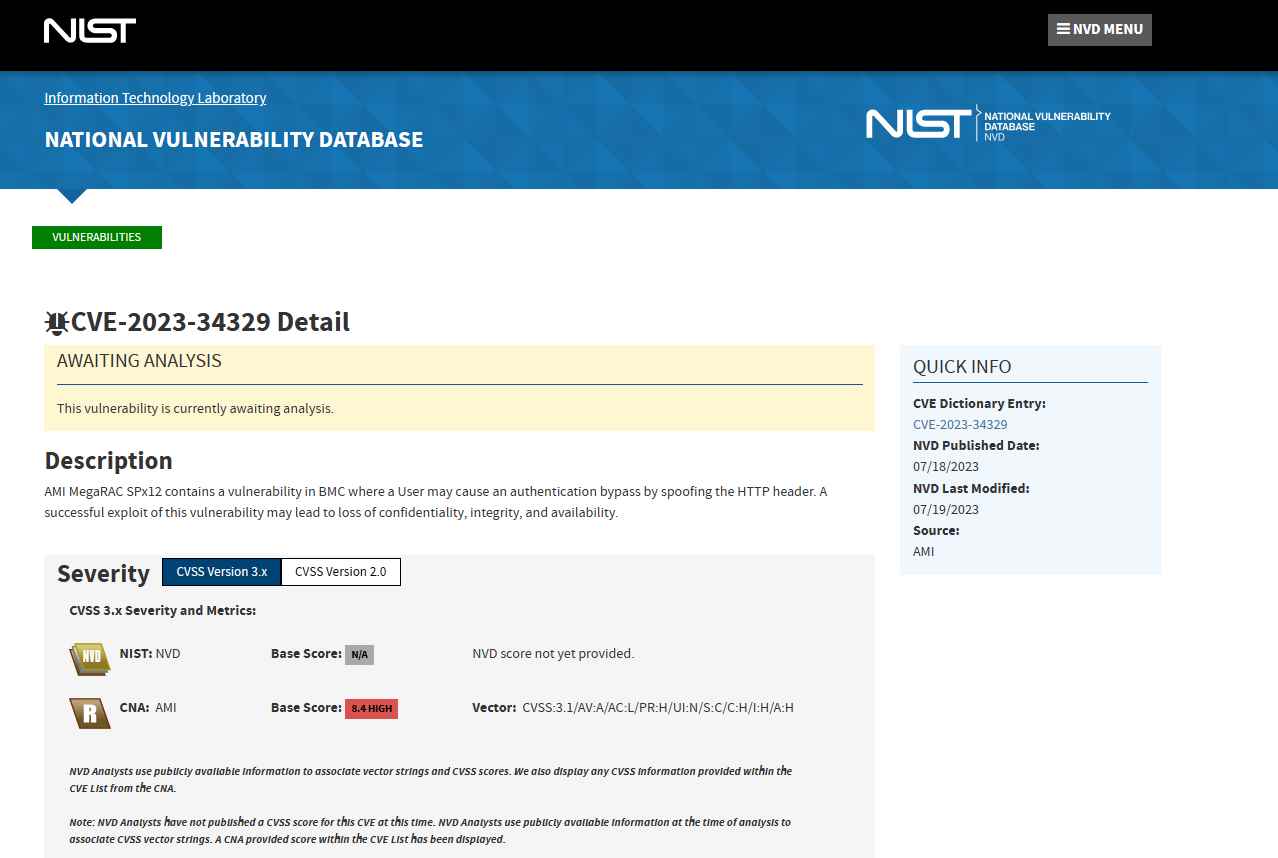
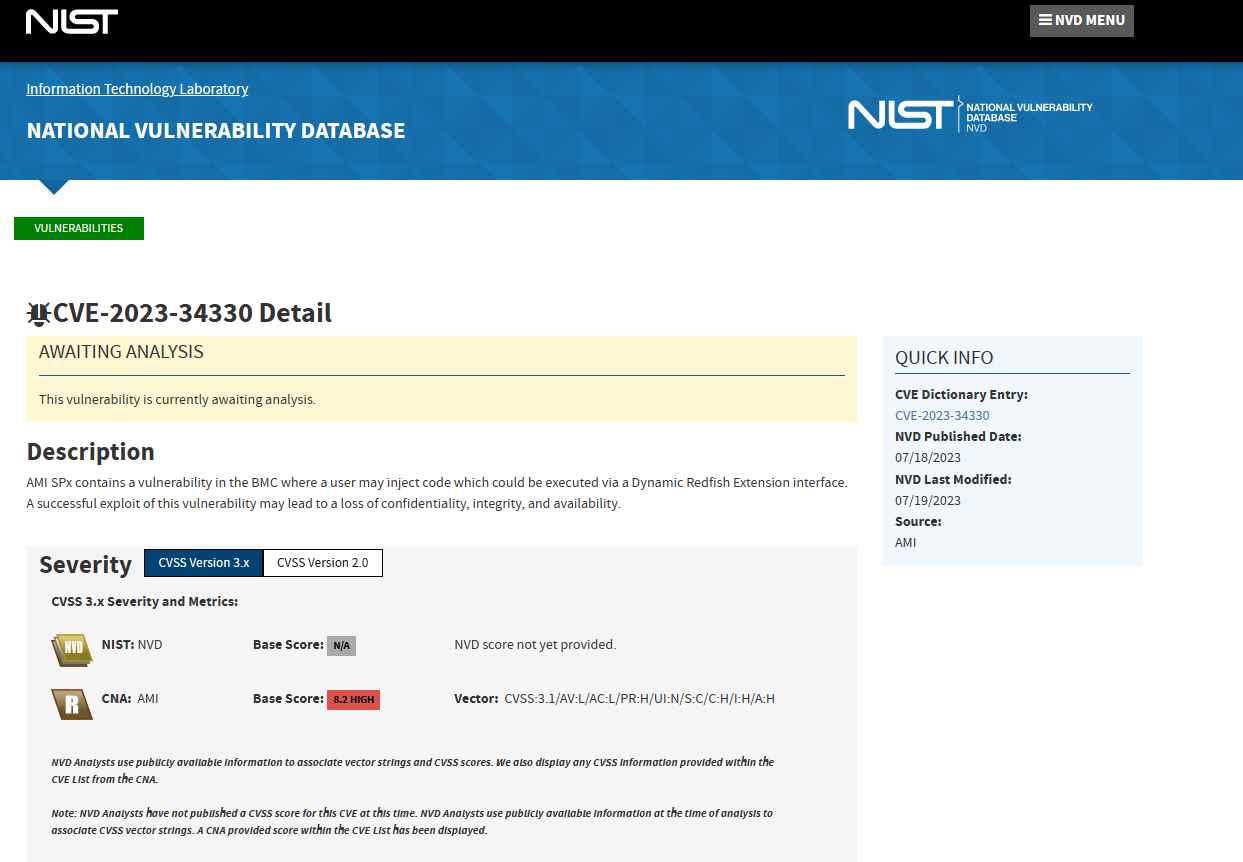
These security flaws vary from High to Critical in terms of their severity, and they include things like unauthenticated remote code execution and unauthorized device access with superuser capabilities. They are exploitable either by remote attackers who have access to Redfish remote management interfaces or from inside a host operating system that has been hacked. Redfish is the replacement to conventional IPMI and offers an API standard for the control of a server’s infrastructure as well as other infrastructure that supports contemporary data centers. Redfish was developed by Intel. Redfish receives support from practically all of the main server and infrastructure providers, in addition to the OpenBMC firmware project, which is often used in contemporary hyperscale settings.When both of these flaws are combined, a remote attacker with just network access to the BMC management interface and no credentials for the BMC system may accomplish remote code execution by deceiving the BMC system into thinking that the HTTP request is coming from the internal interface. This can be done by chaining the vulnerabilities together. As a consequence of this, the attacker has the ability to remotely upload and run arbitrary code, perhaps from the Internet, provided that the interface is accessible to it.
The supply chain of technology that underpins cloud computing is exposed to a significant risk as a result of these vulnerabilities. In a nutshell, the vulnerabilities that exist inside a component supplier impact a large number of hardware manufacturers, which in turn may be passed on to a large number of cloud services. Because of this, the servers and hardware that an organization directly owns might be at danger, in addition to the gear that supports the cloud services that the business makes use of. They are also able to have an effect on businesses’ upstream suppliers, and as part of an organization’s basic supply chain risk management due diligence, they should be addressed with critical third parties.
BMCs are created with the intention of giving administrators almost complete and remote control over the servers they are responsible for managing. AMI is the industry’s preeminent supplier of BMCs and BMC firmware, serving a comprehensive spectrum of hardware manufacturers and cloud service providers. As a consequence of this, a very large number of devices are impacted by these vulnerabilities, which may make it possible for malicious actors to take control of devices, as well as data centers and the infrastructure supporting cloud services, and inflict harm.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
