Phishing Defense Center (PDC) specialists have just revealed the detection of a phishing campaign in which threat actors pretend to be Skype employees. As mentioned above, the social distancing policy has significantly increased the use of remote communication tools, so hackers have also increased attack campaigns against these services.
In this malicious campaign, hackers use an email address remarkably similar to the email address of authentic Skype notifications. Hackers try to fake a phone number and email address to convince the user that they are being contacted by Skype staff members.
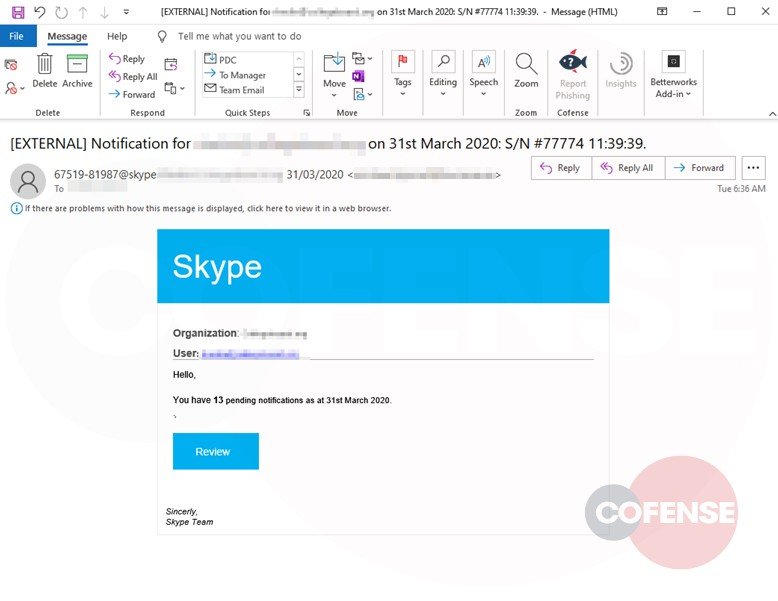
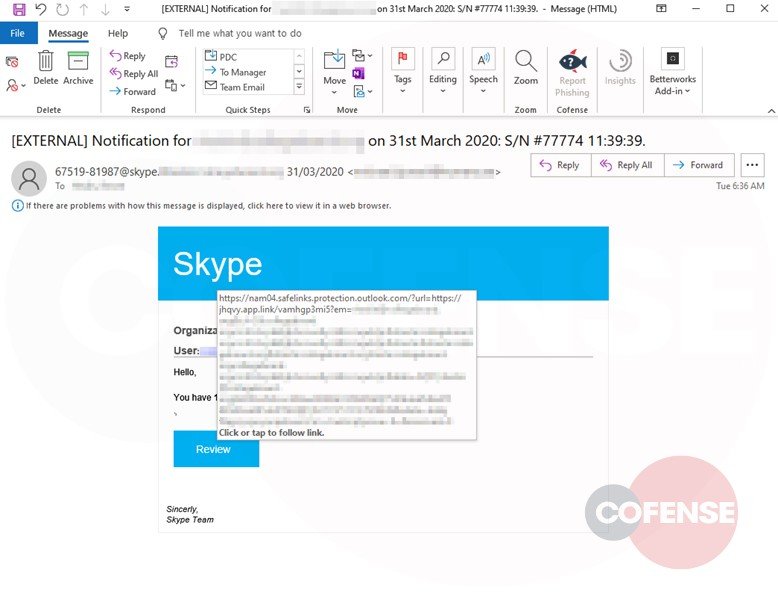
Although the sender’s address may seem legitimate, the actual sender can be found in the return path shown as “sent from”, which is also an external compromised account. Although there are many ways to exploit a compromised account, for this phishing campaign, the threat actor chose to use it to send even more phishing messages pretending to be a trusted colleague or friend.
It is actually very common to receive emails about pending notifications for various services. Hackers expect users to count on this, so they’ll take steps to view notifications. Due to the need to stay and contact with their colleagues, users constantly check the notification button without identifying anomalous behavior.
- When clicked “Review”, users will be redirected via an application link: hxxps://jhqvy[.] app[.] link/VAMhgP3Mi5
The attacker decided to use a .app top-level domain to host their attack. This TLD is backed by Google to help app developers share their apps securely. One advantage of this top-level domain is that it requires HTTPS to connect to it, adding security to both the user and the developer. While this is a useful feature, it also works for hackers.
The inclusion of HTTPS means adding a lock to the address bar, which most users have been trained to trust. Because this phishing site is hosted through Google’s TLD .app, it displays a trusted icon on the site.
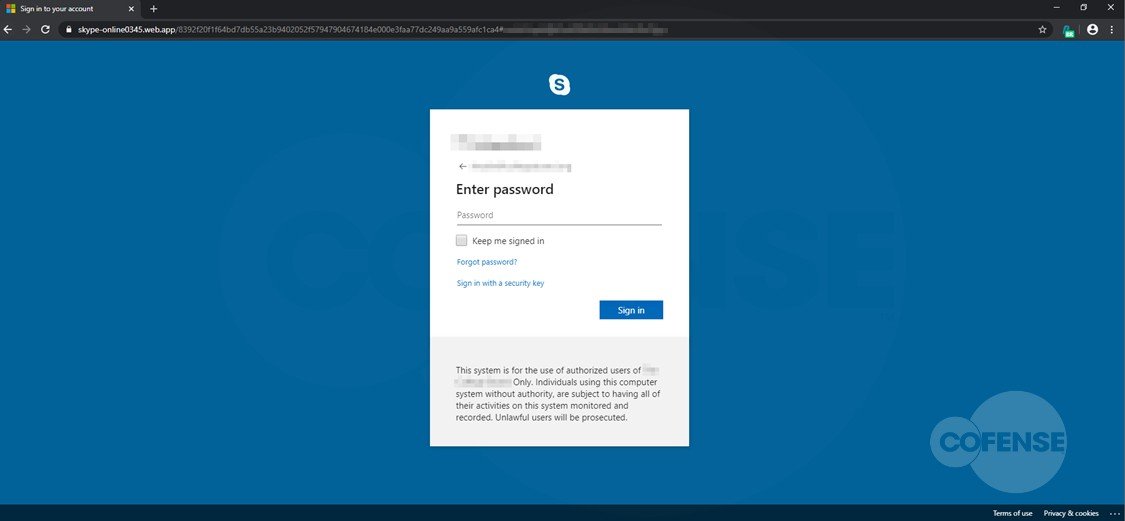
Clicking the link shows the user an impersonation of the Skype sign-in page. If a user familiar with cybersecurity topics inspects the URL, it will be noticeable that the URL contains the word Skype (hxxp://skype-online0345[.] web[.] app).
To add even more authenticity to this scam, attackers add the recipient’s company logo to the login box, as well as a “disclamer” at the bottom that warns that this page is only 2for authorized use” by company users, so it is highly possible for targeted employees to fall into the trap.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
