Cybersecurity specialists report the detection of a critical vulnerability in Apple AirTag whose exploitation would allow threat actors to find the phone number of a target user and even redirect them to an iCloud phishing site and other legitimate platforms.
Apparently, all this is due to the device’s “Lost Mode”, which allows users to alert Apple when their AirTag is misplaced. Enabling this feature generates a unique URL in https://found.apple.com and allows users to enter a personal message and contact number; in these cases, anyone who finds an AirTag device could scan it with a smartphone, thus finding the Apple URL.
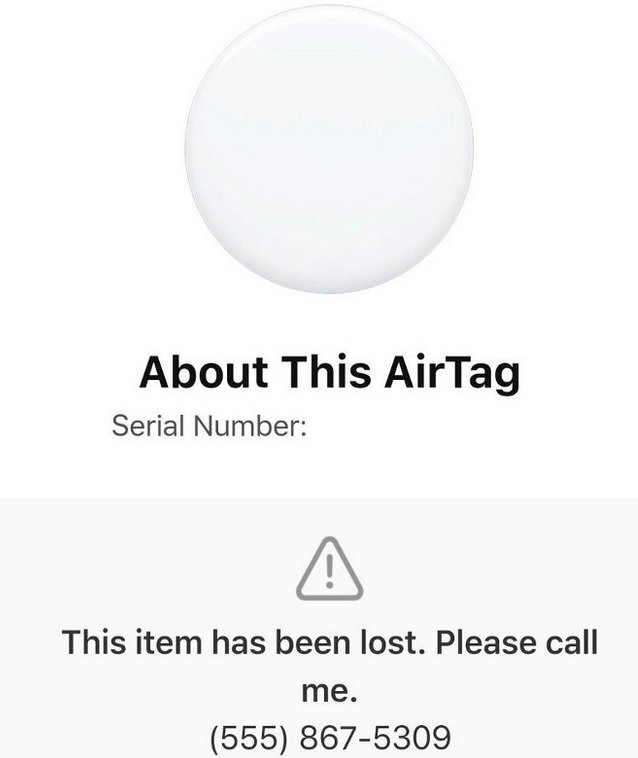
This feature is designed so that when a person finds a misplaced AirTag, they have a way to contact their owner by displaying their phone number and URL. This data appears without the need for the person who finds the device to meet any authentication requirement, although threat actors could compromise this process for malicious purposes.
Lost Mode is not protected in any way, so a malicious user could inject code into the information fields of this feature and intentionally leave the device in some public place to make the user who finds it visit a phishing website.
This error was reported by researcher Bobby Raunch, who in his publication described the Apple AirTag as potential Trojan horses, within reach of any cybercriminal group for less than $ 30 USD: “I do not remember other cases in which a simple low-end device can become a sophisticated weapon,” adds the expert.
Although this attack seems somewhat complex and depends on many variants and extensive collaboration of the potential victim, threat actors always find a way to make these baits attractive, something demonstrable and somewhat common due to the simplicity of the attack.
Cybersecurity experts have reported multiple cases of malware infections from USB devices found on the street, shopping malls, public transportation, and offices; for these attacks, threat actors typically leave these devices with labels like “payroll” or “cryptocurrency,” which could be appealing to whoever comes across one of these pieces of hardware.
The AirTag attack starts from the same premise and can be a considerable risk to the safety of anyone. So far Apple has not commented on the matter.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
