In a report released a few hours ago, Microsoft announced the launching of some security updates for Exchange Server that will fix multiple high severity and even critical flaws. The company reports that successful exploitation of these failures could trigger Remote Code Execution (RCE) scenarios, a joint alert from the National Security Agency (NSA) mentions.
As mentioned above, these flaws are highly severe and a recent wave of hacking related to these findings has been detected, so experts recommend users of affected deployments to update as soon as possible.
Failures appear to reside in versions of Exchange Server released between 2013 and 2019, and although no cases of exploitation have been reported in real-world scenarios, the company recommends users evaluate the security of their systems, as the exploit campaign remains active: “These flaws were recently discovered and are being exploited by threat actors” , the NSA notes.
The report refers to four critical flaws and all exploitation scenarios lead to remote code execution. The update package fixed a total of 108 failures, five of them considered zero-day. NSA experts point out that there are two methods for applying updates in Exchange Server:
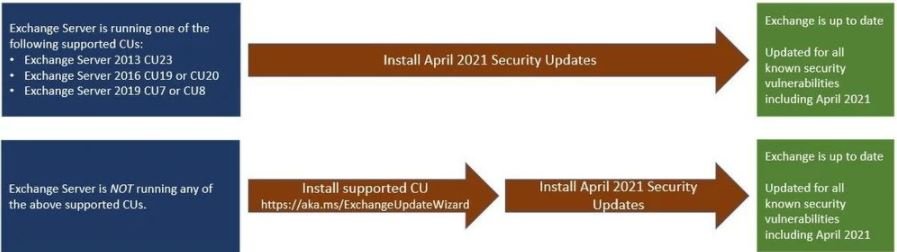
It should be noted that manual application of updates requires the installation of the Windows Installer .MSP from an elevated command prompt.
The company recommends that affected organizations use Health Checker commands to verify the presence of engagement indicators. This script also allows administrators to verify whether any of their Exchange servers need to be upgraded.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
