Cybersecurity specialists report that a Chinese hacking group is exploiting a critical zero-day vulnerability in Zimbra in order to access exposed email inboxes and obtain information related to European governments and news agencies. The attacks were detected last month by security firm Volexity.
Investigators mention that the attack began in late 2021 and was deployed in two stages; to begin with, the attackers sent a seemingly legitimate email starting a recognition campaign and listing active email accounts. The hackers then included a link in the body of the email redirecting users to a remote website where malicious JavaScript code would execute a cross-site scripting (XSS) attack against the Zimbra platform.
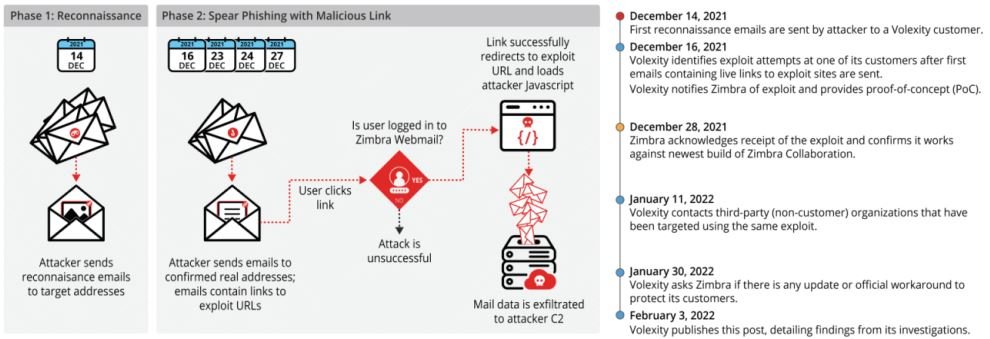
The researchers mention that the code abuses a bug in Zimbra email clients running versions 8.8.15 P29 and P30, which would allow the theft of session cookies. Threat actors could connect to a compromised account to access stored emails, as well as send phishing messages to other users and deliver malware very easily.
While there are currently more than 33,000 Zimbra servers connected to the Internet, experts mention that the zero-day vulnerability does not work against Zimbra 9.x versions, so the attack surface is much smaller than initially thought.
Volexity concluded by mentioning that, based on the characteristics of the attack, it was impossible to determine which threat group is behind this attack, so they only identified it as TEMP_Heretic. Still, investigators believe the attack was orchestrated by a Chinese threat actor.
System administrators using Zimbra are encouraged to review the full report to determine the best security measures that can be applied to prevent an attack.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
