The Lapsus$ hacking group is abusing stolen NVIDIA code signing certificates to inadvertently sign malware on vulnerable Windows deployments. This week, NVIDIA confirmed that it suffered a cyberattack that allowed threat actors to access sensitive information of its employees.
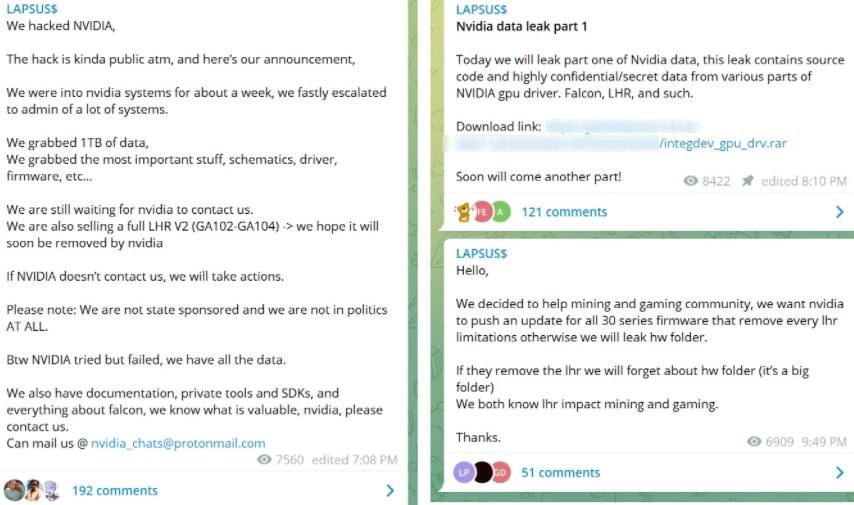
The hackers, allegedly operating from Latin America, claim to have stolen files equivalent to 1 TB during the incident, beginning to leak them on illegal forums on the dark web after NVIDIA refused to pay a ransom. The leak includes two stolen code signing certificates used by NVIDIA developers to sign their drivers and executables.
These certificates allow developers to digitally sign executables and drivers so that the Windows system can verify ownership of the file and whether a third party has manipulated the payload. To increase system security, Microsoft also requires kernel-mode drivers to be signed with code before they are loaded into the operating system.
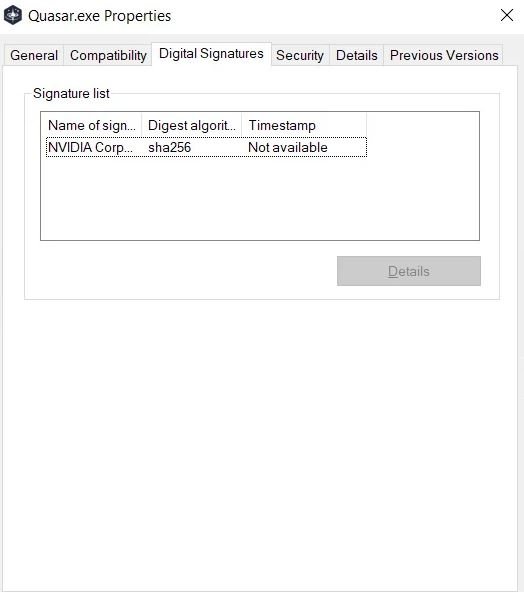
Shortly after the attack was confirmed, cybersecurity specialists began detecting that the certificates were being used to sign malware and other hacking tools used by cybercriminals. Samples uploaded to VirusTotal indicate that the stolen certificates were used to sign various malicious programs, including Cobalt Strike beacons, Mimikatz, backdoors, and remote access Trojans (RAT).
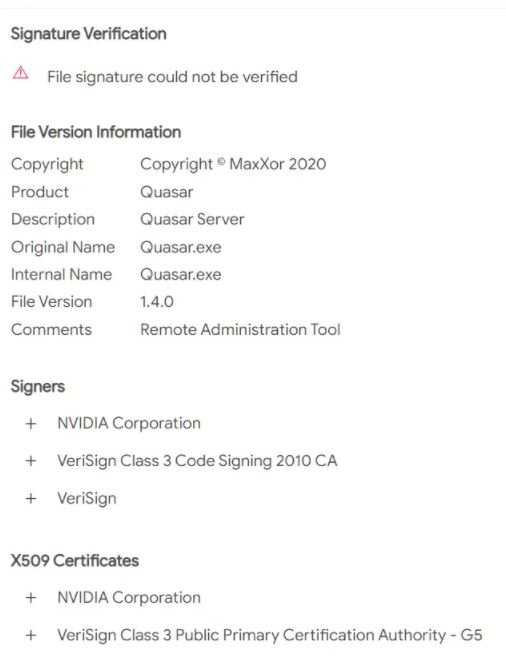
Stolen certificates use the following serial numbers:
- 43BB437D609866286DD839E1D00309F5
- 14781bc862e8dc503a559346f5dcc518
Some of the files were probably uploaded to VirusTotal by security researchers, but others appear to be used by threat actors for malware campaigns. Although the stolen certificates are expired, Windows still allows them to be uploaded to the operating system, giving threat actors the advantage of making their malicious payloads look like legitimate NVIDIA content, so the security threat is still active.
Administrators of Windows systems with NVIDIA components are encouraged to configure Windows Defender application control policies to determine which NVIDIA drivers can be loaded into the system and prevent malware from entering.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
