A couple of months ago, the U.S. National Credit Union Administration (NCUA) issued a report asking thrift cooperatives to take proactive measures in the face of potential cybersecurity threats, as in such a complex environment financial institutions become highly attractive targets for malicious hackers.
The NCUA’s fears are not unfounded; recent reports claim that more than 60% of savings cooperatives do not have adequate email security measures to detect phishing messages, while more than 90% of these institutions lack up-to-date security mechanisms.
Apparently, hacking groups around the world are exploiting these cybersecurity gaps to deploy phishing campaigns and obtain end-user credentials. A report from security firm Avanan details an increase in social engineering campaigns using the name and image of local savings cooperatives seeking access to monetary funds.
These attacks can come in various variants, whether hackers pose as bank employees or business partners by requesting bank transfers and sending unsolicited documents from the affected organization.
In the example shown below, threat actors are trying to supplant a local credit union.
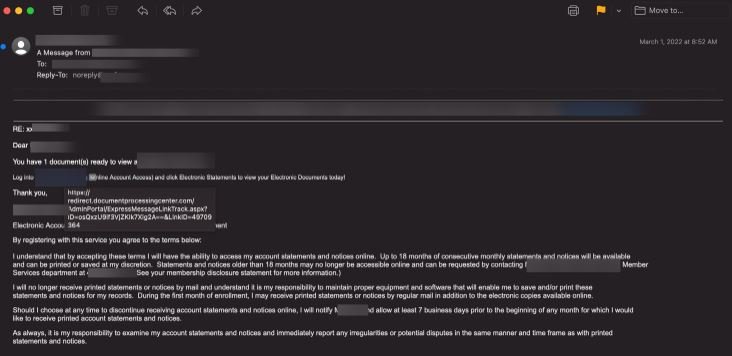
The message is displayed as a document notification and includes a link that will redirect the victim to a fraudulent website where their login credentials will be intercepted.
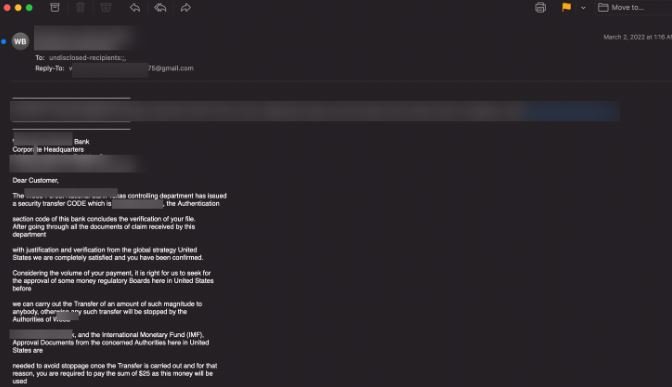
This variant of the attack opts for a more aggressive stance, with cybercriminals requesting money to stop an alleged transfer:
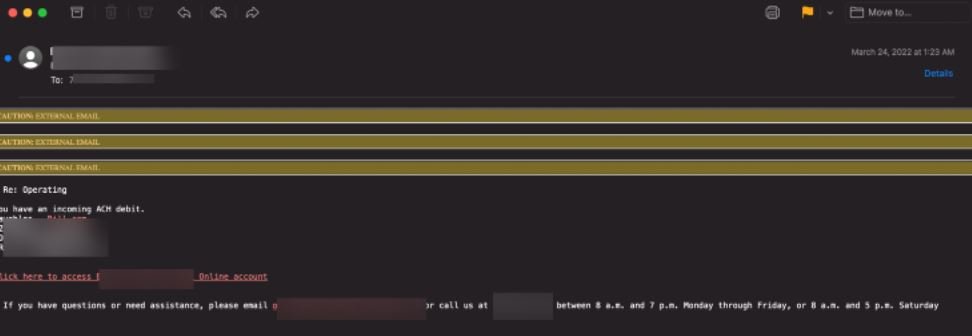
Other examples of the attack include messages related to an incoming debit to the affected user’s account:
Cybersecurity specialists mention that, despite their low complexity, phishing attacks are still highly successful, mainly because victims do not usually have the necessary knowledge to identify a malicious email.
In the case of savings cooperatives, it is estimated that cybercrime could generate losses of up to $1.2 million USD in each attack, so the risk is considerable and it would be best to start considering appropriate prevention measures.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
