Hackers in Belarus are focusing their attention on foreign embassies in the hopes of stealing papers, recording audio, and tracking victim keystrokes. Researchers from the cybersecurity company ESET gave the perpetrators the moniker “MoustachedBouncer” because of their connections to the government of Belarus.
The organization has been active since 2014, but in 2020 it changed its strategy and started carrying out operations that experts refer to as “adversary-in-the-middle” attacks, or AitM attacks for short. A sort of cyberattack known as AitM occurs when malicious actors interrupt the authentication process that takes place between users and a service in order to steal data or compromise identities. ESET has identified four embassies that have been compromised as a result of the attack, two of which are located in Europe and one each in South Asia and Africa.
The TTPs of the group had a remarkable evolution over the course of time, and the group was active from 2014 to 2022. yet, it is noted that the organization will continue to use AitM attacks in 2020; yet, the remarkable part about this situation is that the targeted verticals will not change.MoustachedBouncer exploits ISPs to trick users in selected IP ranges into visiting fraudulent URLs that seem like legitimate Windows Update download sites. These URLs are listed below:-
updates can be found at http://updates.microsoft.com.
Users are offered with a button that is labeled “Get updates,” and when they click on it, malicious files are downloaded with the use of JavaScript. Victims see false Windows Update sites that include urgent security notifications.
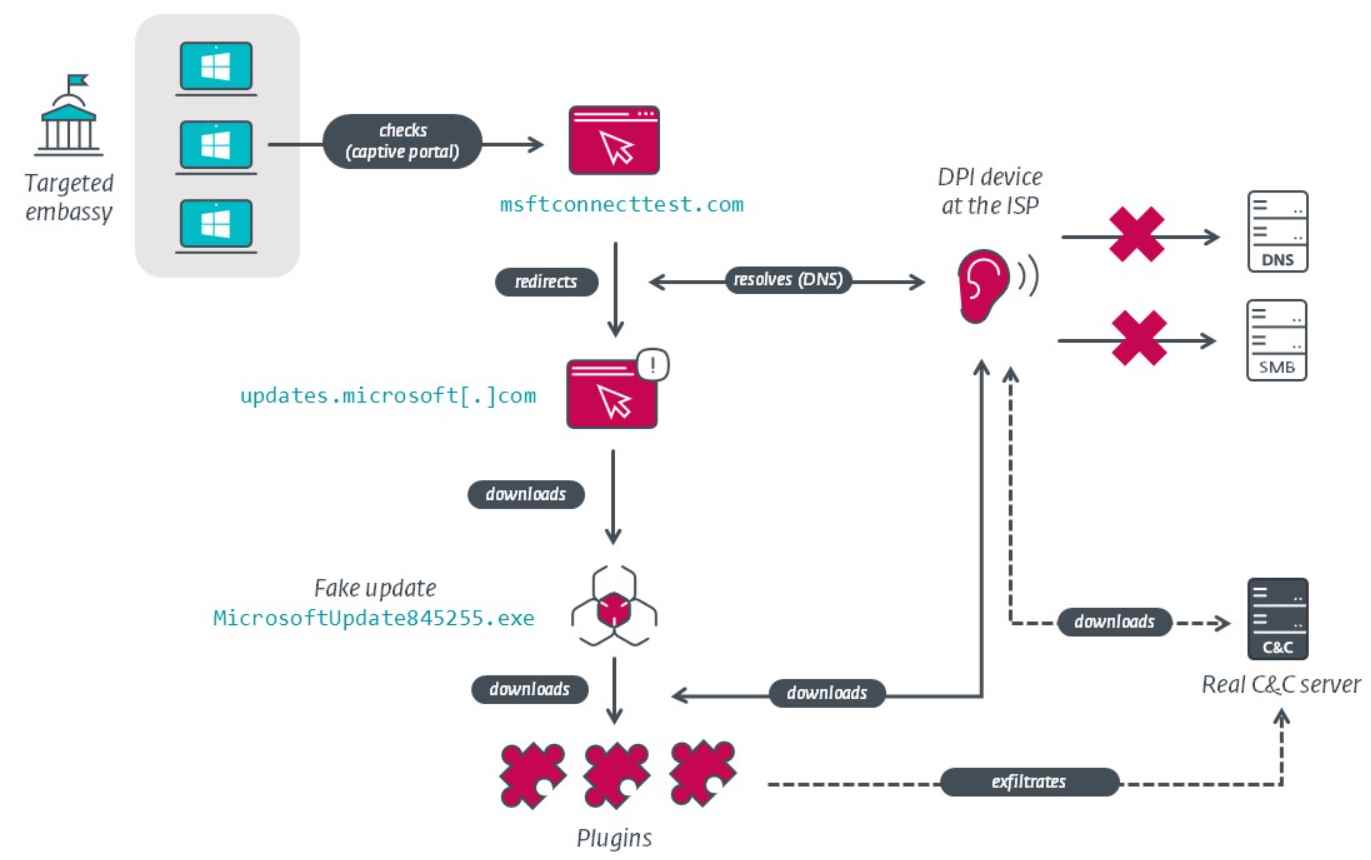
It has been hypothesized that the partnership between MoustachedBouncer and Belarusian ISPs for the development of a legal intercept system is entirely comparable to Russia’s SORM, which was implemented in 2016 as a result of a regulation demanding compliance on the part of telecom carriers.
In a study that was released this week and presented at Black Hat, Faou explained the variety of tools that were used by the hackers to launch the attacks. He gave the programs the names “NightClub” and “Disco.”
NightClub is used in situations when traffic interception is not feasible, such as when embassies employ VPN services to route traffic outside of Belarus. In contrast, Disco is utilized during AitM attacks.
For the purpose of stealing data, NightClub takes use of free email services, most notably the webmail service provided by Seznam.cz in the Czech Republic and the webmail provider Mail.ru in Russia. They are able to snap screenshots, record audio, and keep a track of keystrokes thanks to the tools.
During the course of his investigation into the organization, Faou said that he came across connections between MoustachedBouncer and Winter Vivern, a hacker outfit that is believed to have connections to Moscow.
Faou also discovered connections to the Russian hacker outfit known as Turla, which was named as a suspect in attacks on Ukrainian military forces that used spying software one month ago.In addition to this, NightClub has two core capabilities, both of which are detailed in the following paragraphs:
- Monitoring files
- Exfiltrating data via SMTP (email)
All of these important indicators demonstrate that the threat actor known as MoustachedBouncer is a capable one that aggressively targets diplomats in Belarus by using sophisticated methods for command and control communication.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
