Researchers from the SafetyDetectives team found an exposed AWS S3 bucket that stored personal details about pilots, flight staff and other employees at Turkish flight company Pegasus Airlines. This bucket was linked to PegasusEFB, a tool developed by the airline and used by its pilots for some tasks during flights.
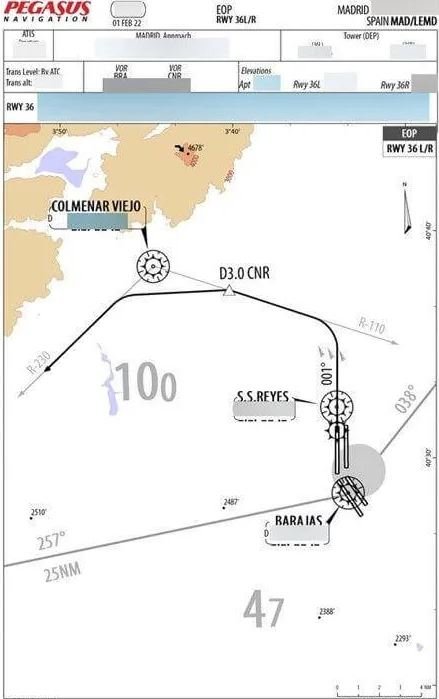
The records breached in the bucket are known as the Electronic Flight Bag (EFB), and include flight charts, navigation material and personal information about the crews on the various flights. The leak also includes EFB’s source code, in addition to raw passwords and keys that would allow the manipulation of sensitive files.
The exposed AWS deployment contained about 23 million files in the bucket, equivalent to 6.5 TB of data. According to the researchers, the leak of these records could compromise the safety of all Pegasus passengers and crew members around the world, in addition to impacting other airlines using the PegasusEFB system.
Each EFB contains detailed data, such as:
- Acceptance forms, including minor issues found during pre-flight checks
- Flight charts and revisions
- Spreadsheets with airports, flights, crew shifts, and other details
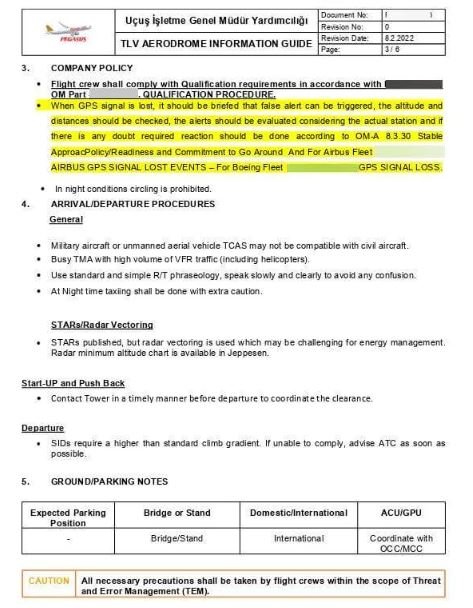
- Internal documents and memorandums
- Safety integrity level logs containing regulations and source code
Besides, the AWS bucket contained airline staff records, including:
- ID photos
- Signature

Investigators notified Pegasus of the leak on March 1, 2022, sending a second message on March 20 after receiving no response. The incident was responsibly disclosed on March 24, after notifying the company. Pegasus Airlines later acknowledged the leaking and shut down the illegitimate access. It is unknown whether any threat actors were able to access the compromised information.
As with any data breach, this incident could facilitate the deployment of phishing, social engineering, or business email compromise (BEC) campaigns. While the nature of the compromised information is not considered critical, the affected company is advised to apply additional security measures to prevent related security incidents.
Moreover, airline employees are advised to ignore any requests for confidential information, whether via email, phone or text message, as the security risk is considered active.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
