A recent report details the detection of a critical vulnerability in virtual private network (VPN) solutions developed by Fortinet; the flaw could be exploited to infect systems compromised with the Cring ransomware variant and allow malicious actors to perform further attacks. This variant of encryption malware was first reported in early 2021 and has also been identified as Crypt3r, Ghost and Phantom.
The report mentions that ransomware operators send custom samples from Mimikatz and CobaltStrike to inject Cring payloads via Windows CertUtil, Microsoft’s legitimate certificate manager.
According to Kaspersky experts, threat actors search for and exploit Fortigate SSL VPN services vulnerable to exploiting the flaw tracked as CVE-2018-13379: “This campaign primarily appeals against business environments; at least in one of the cases analyzed, the infection caused the temporary closure of the industrial facilities of an affected company,” the experts say.
ATTACK PROCESS
Malicious hackers perform side movements on the compromised network to steal a Windows user’s credentials using Mimikatz. Subsequently, threat actors use CobaltStrike to send the payload to the victim’s device.
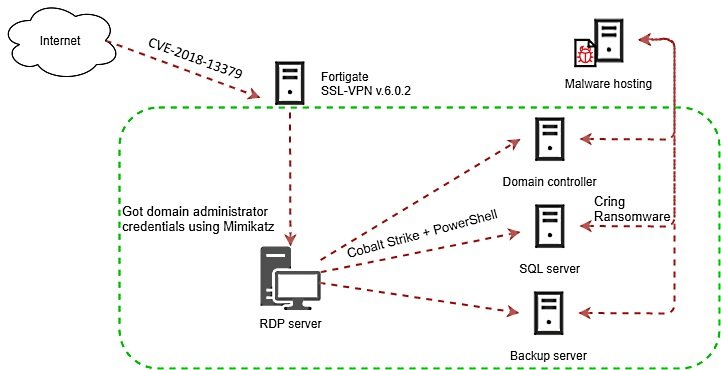
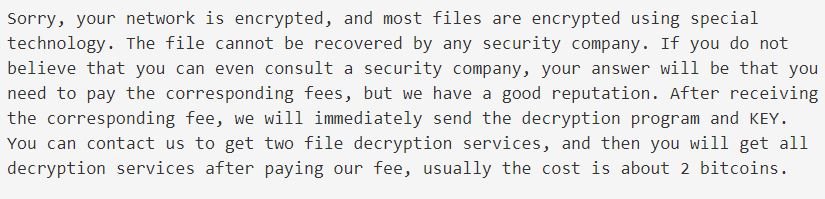
Apparently this malware variant encrypts only a few files on the affected device, while deleting backups and stopping Microsoft Office and Oracle Database processes. Subsequently the ransom notes appear notifying victims that their networks have been infected and must pay the ransom.
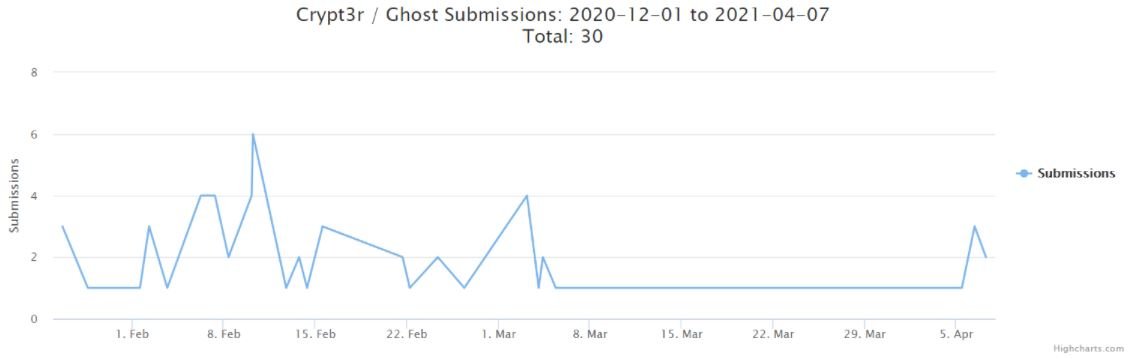
The operators of ID-Ransomware, a platform that collects the most up-to-date information about this attack variant, point out that at least 30 samples of this variant have already been published, noting that publications began in late January 2021.
This is not the only active risk threatening users of non patched Fortinet solutions. A few days ago the Cybersecurity and Infrastructure Security Agency (CISA) issued a security report detailing the activity of a hacking group targeting Fortinet VPN devices vulnerable to the exploitation of CVE-2018-13379. As in Cring’s attacks, exploiting this flaw would allow threat actors to enter compromised business networks.
“Cybercriminals often abuse critical vulnerabilities to perform denial of service (DDoS) attacks, ransomware infections, SQL injections, phishing campaigns, among other risky scenarios,” the Agency says.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
