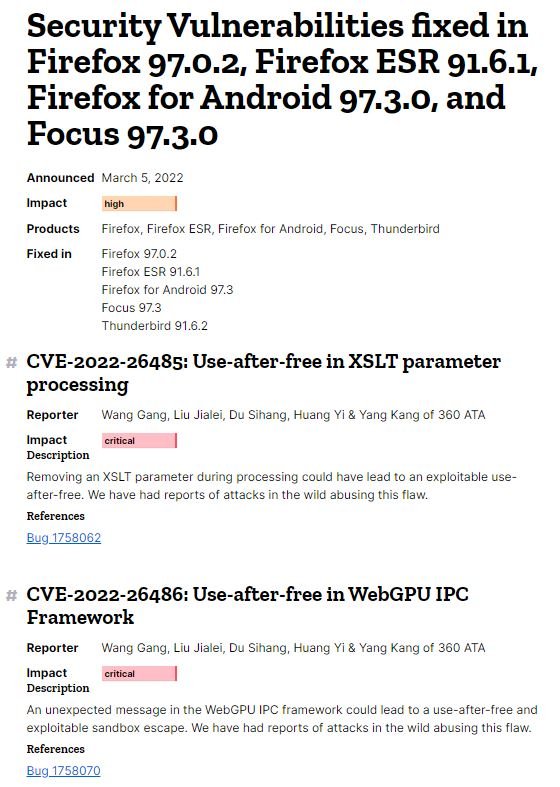
Mozilla security teams announced the release of an emergency update to address two zero-day vulnerabilities in the Firefox browser recently exploited in the wild. Tracked as CVE-2022-26485 and CVE-2022-26486, the failures are described as use-after-free errors and were reported by Qihoo 360 specialists.
According to the report, the first vulnerability can be exploited by removing an Extensible Stylesheet Language Transformations (XSLT) parameter during processing, while the second flaw is exploited by an unexpected message in the Inter-process Communication (IPC) WebGPU framework.
Although Firefox developers did not reveal more details about the exploitation attempts detected so far, cybersecurity specialists point out that use-after-free flaws generally allow threat actors to execute arbitrary code on affected systems.
The flaws were addressed with the release of Firefox 97.0.2, Firefox ESR 91.6.1, and Firefox for Android 97.3.0 and Focus 97.3.0, according to Mozilla’s report. It is possible that the company will share more information about the exploitation of these flaws once they consider that the risk of attack has decreased.
During the last few years, multiple zero-day vulnerabilities have appeared in Firefox, so the browser’s developers have had to work at a forced pace to mitigate the risk of exploitation. Moreover, Google Project Zero has identified at least 7 zero-day vulnerabilities in this browser since 2014.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
