Cybersecurity specialists from the firm Website Planet report the detection of a completely unprotected database that guarded a total of 12,976,279 records belonging to FOX News, including usernames, employee identifiers and more confidential details.
According to the report, many of these exposed records were labeled “prod,” an abbreviation for “production” or “live recordings.” The data breach was reported to the affected company and access to the exposed database was restricted shortly thereafter.
In addition to the records mentioned above, the database included information such as:
- FOX CRM logs that expose user IDs, event logs, hostnames, IP, interface, and device data
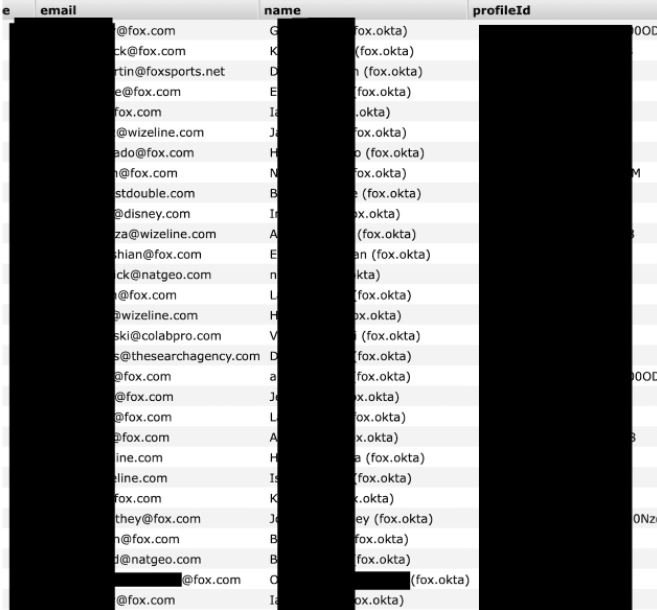
- Hundreds of email addresses, including 700 internal @fox.com addresses
- Operation details from the backend and File Transfer Protocol (FTP) links
Database indexes make clear the type of information collected and stored. The researchers found a total of 102 folders with titles such as user roles, user editor, usuarios_v2, video editor, and other job names related to the news platform’s content.
As mentioned above, the leak involves more than 700 internal email accounts of @Fox.
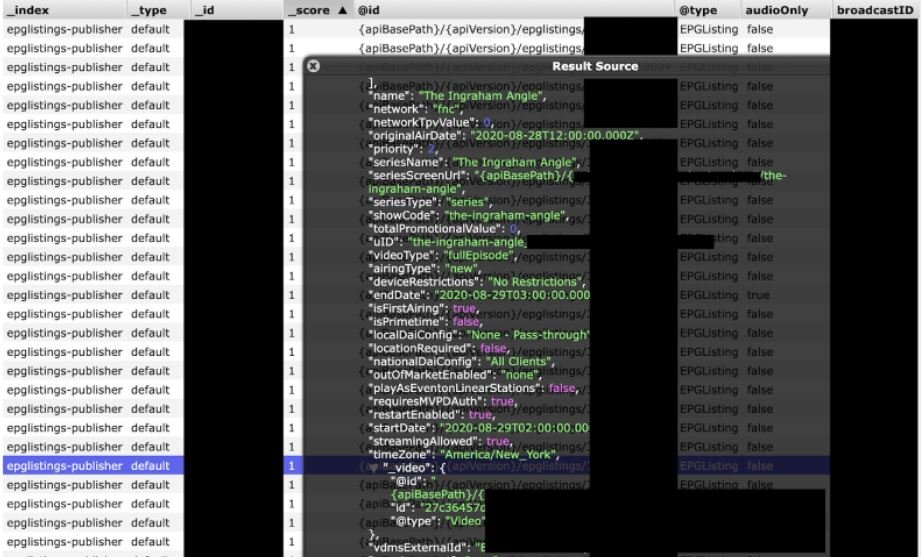
The following screenshot shows a detailed view of how the logs include detailed information from FOX News programs, including individual episode identifiers, location of files in storage, internal IDs, and other details.
FOX News responded to this report by mentioning that this incident is being followed up, although they specify that the database is not connected to a specific production environment. Still, the news platform’s investigation will remain active until the causes of the leak are found.
As in any data breach incident, the users involved could be exposed to sophisticated phishing campaigns, social engineering, and identity fraud. Although the news agency has not commented on the matter, it is expected that users will receive some kind of protection against potential fraud attempts.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
