It has been confirmed that the cyberattack targeting the US-based firm Sitel has resulted in a data breach affecting Okta, an identity and access management company that subcontracted Sitel for some of its operations. Reports about this attack began circulating after hackers from the Lapsus$ group posted some screenshots showing what looked like Okta’s confidential information.
In this regard, Okta mentions that hackers could have affected up to 366 customers during a five-day period in January, during which time the attackers had access to a Superuser/Okta.com Administrator account, allegedly obtained from a Sitel customer service engineer. Okta believes the outsourced company made some mistakes and failed to properly report the incident.
Sitel confirmed the attack on Tuesday, mentioning that an investigation had already been launched and offering its full cooperation to law enforcement, ensuring that more details would be shared as soon as the investigation allowed. However, the company reported that the incident was related only to the legacy Sykes network.
Researchers report that threat actors accessed a spreadsheet where Sitel improperly safeguarded access credentials for their domain administrator accounts. The company mentions the document only listing Sykes’ account names, though it did not confirm the presence of passwords.
In its report, Sitel assures that the risks derived from this incident have already been mitigated, although the investigation will not be interrupted until all possible information is found.
Lapsus$ never stops
After a couple of weeks of inactivity and the alleged arrest of some of its members, the hacking group allegedly controlled from Latin America has reappeared, compromising the information of Okta and other companies.
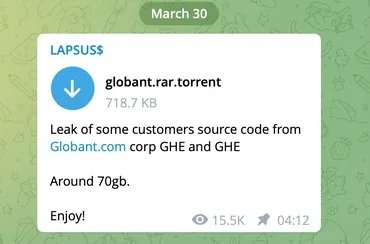
This morning, the hacking group claimed to have compromised the systems of Globant, an Argentine firm dedicated to software development. Threat actors claim to have stolen sensitive source code, which is now available for download in a torrent file larger than 70 GB.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
