A security report states that PayloadBIN, a recently detected malware variant, was developed by the cybercriminal group Evil Corp, also identified as Indrik Spider. This group initially operated as an affiliate of the ZeuS botnet, although it eventually began its own malicious campaigns, based on the distribution of banking Trojans via phishing emails.
Subsequently, seeing the huge profits that ransomware attacks can generate, Evil Corp hackers began operating a variant of ransomware identified as BitPaymer, delivered via the Dridex malware.
The inordinate growth of these attacks began to attract the attention of law enforcement agencies in the U.S., so organizations infected with ransomware stopped paying ransoms to Evil Corp hackers because of the possibility that this decision would lead to legal problems and the imposition of fines from the Treasury Department.
To try to escape the authorities’ crosshairs, Evil Corp hackers began using other names for their ransomware operations, including WastedLocker, Hades and Phoenix, a variant that was detected in the recent attack on insurance company CNA.
In what seemed like an isolated event, the operators of the Babuk ransomware group announced that they would stop operating ransomware variants to focus on data theft, even changing the appearance of their website to reveal that, from now on, the group would be identified as Payload BIN.

Last week a researcher found a new ransomware sample labeled payloadbin that was immediately linked to babuk’s name change. Upon completion of your installation, this malicious payload adds the .PAYLOADBIN to encrypted files.
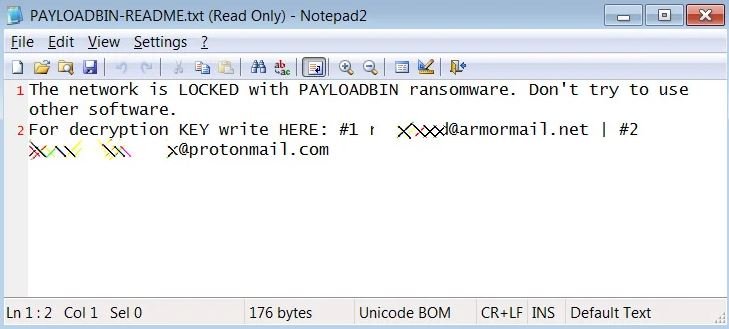
After infection it also publishes a ransom note in a file titled ‘PAYLOADBIN-README.txt’.
While this seemed like just another sample of a new ransomware group, ID Ransomware researcher and founder Michael Gillespie confirmed that this is also one of the variants operated by Evil Corp’s hackers.
Ransomware specialist Fabian Wosar agrees with Gillespie, as well as considering that Evil Corp was only trying to take advantage of Babuk’s announcement, posing as a group of hackers that is not sanctioned by the US authorities. Because this incident was attributed to an unsywarned hacking group, most of the victims surely negotiated a ransom payment without knowing they were dealing with Evil Corp.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
