Rapid7 cybersecurity specialists report that thousands of Zyxel firewalls could be exposed to remote attacks due to a recently detected vulnerability. While the company has already released the corresponding patches, users of the affected products were not immediately alerted, thus increasing exploitation risk.
Tracked as CVE-2022-30525, the vulnerability resides in the Zyxel firewalls of the ATP, VPN, and USG FLEX series. According to the report, the flaw could have been exploited by unauthenticated threat actors to lead to arbitrary code execution in the affected implementations.
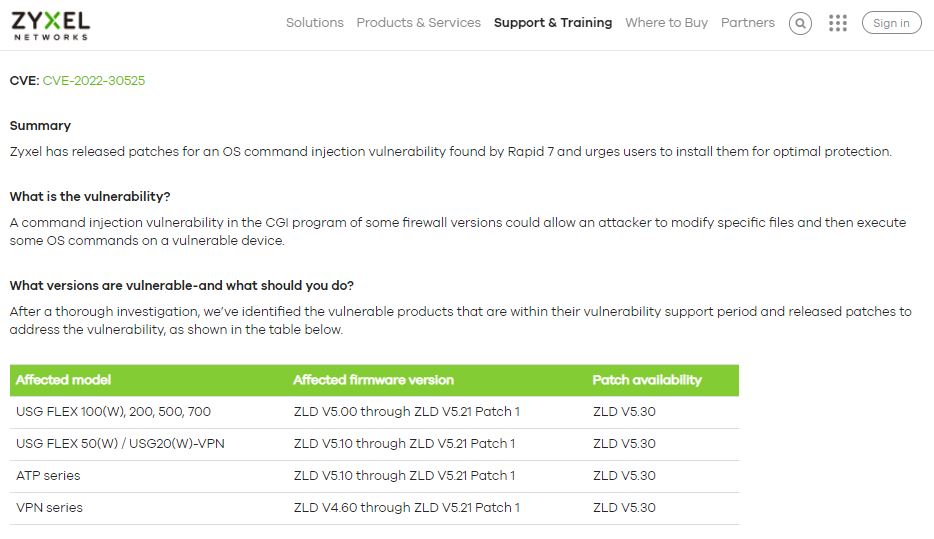
Rapid7 describes this flaw as an unauthenticated command injection issue that could be exploited through the HTTP interface of a vulnerable device; the firm’s report includes a Metasploit module to exploit the flaw and obtain a reverse shell. Zyxel received the report in mid-April and patched the issue a few days later.
The vulnerability was publicly disclosed on May 12 by both companies. In the disclosure report, Rapid7 stated: “This patch release is tantamount to releasing details of the vulnerabilities, since attackers and researchers can trivially reverse the patch to learn precise exploitation details, while defenders rarely bother to do this,”
Although the cybersecurity community sets a 90-day deadline for public disclosure of vulnerabilities, both Zyxel and Rapid7 believe that early disclosure of this flaw will make it easier to detect attack attempts, and that this practice helps raise awareness of specific security risks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
