In early 2022, Avast specialists discovered a new ransomware variant delivered in conjunction with the HermeticWiper wiper malware in some attacks, mainly in Ukraine. Further analysis of this security threat revealed a severe weakness in the encryption scheme of this variant, identified as HermeticRansom, making it possible to crack it without having to pay hackers.
According to the researchers, the ransomware is written in the GO programming language. When running on the target system, the malware starts searching for potentially valuable files on local drives and network shares, specifically looking for files with the following extensions: .docx .doc .dot .odt .pdf .xls .xlsx .rtf .ppt .pptx .one.xps .pub .vsd .txt .jpg .jpeg .bmp .ico .png .gif .sql.xml .pgsql .zip .rar .exe .msi .vdi .ova .avi .dip .epub.iso .sfx .inc .contact .url .mp3 .wmv .wma .wtv .avi .acl.cfg .chm .crt .css .dat .dll. cab .htm .html and .encryptedjb.
Another characteristic feature of HermeticRansom is that it avoids encrypting files in Program Files and Windows folders in an attempt to keep the affected system running.
This ransomware creates a 32-byte encryption key for each compromised file, which are encrypted by blocks of 1048576 bytes. During the process a maximum of 9 blocks are encrypted and any data that exceeds 9437184 bytes is left in plain text.
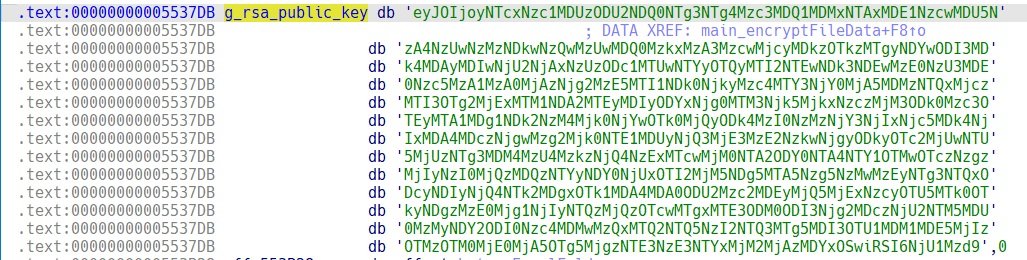
Each block is encrypted by AES GCM symmetric encryption. After data encryption, the ransomware adds a file queue containing the encrypted file key RSA-2048. The public key is stored in the binary as a Base64-encoded string.
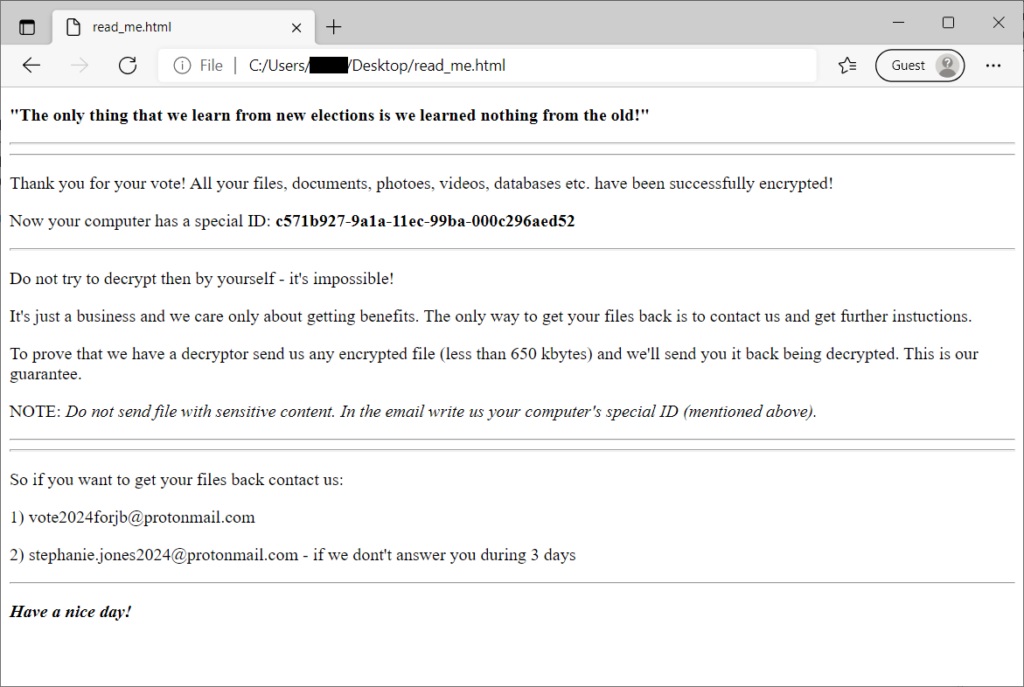
Upon completion of the encryption process, the affected user will find a file named “read_me.html” in the user’s desktop folder:
While the researchers did not share great details about the vulnerability in the HermeticRansom encryption process, they announced the development of a tool capable of removing the infection from the compromised files and regaining access to the information without having to pay any ransom. To get started, the tool must be downloaded from the official Avast platforms:
Subsequently, you only have to run the executable file. This file starts in the form of a wizard, which guides you through the configuration of the tool:
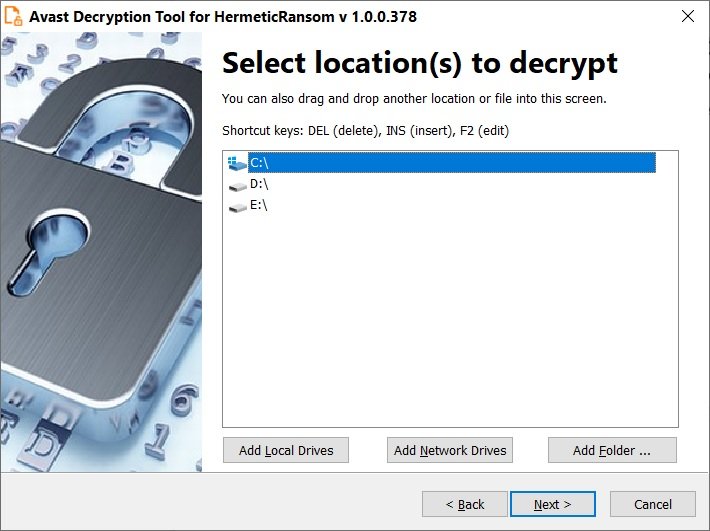
When launching the tool, select the list of locations where you want the decryptor to work or simply choose the default list of locations:
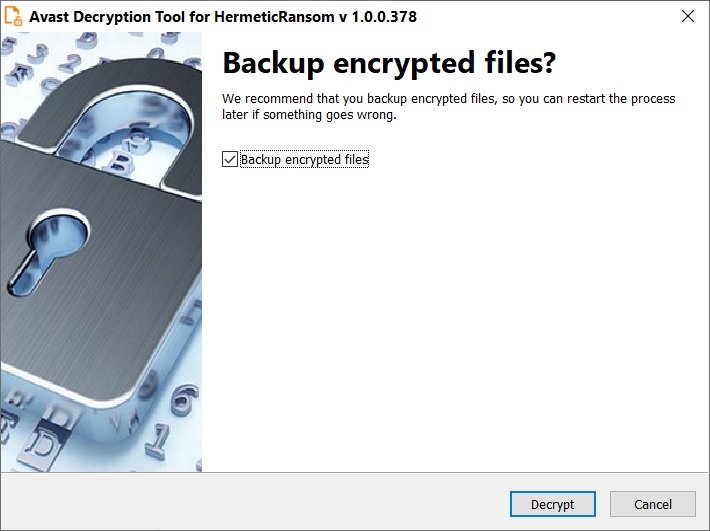
At the end of the recovery process, you may also choose to create a backup of your information, in order to protect against other similar incidents.
Para conocer más sobre riesgos de seguridad informática, malware, vulnerabilidades y tecnologías de la información, no dude en ingresar al sitio web del Instituto Internacional de Seguridad Cibernética (IICS).
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
