Researchers at security firm Avanan report detecting a hacking campaign targeting Microsoft Teams users through malicious executables. According to experts, these files placed in Teams conversations can write data to the Windows registry, install DLLs, and even create links for automatic malware management.
In their report, the specialists claim to have detected a few thousand cases since the beginning of 2022, in addition to mentioning that this campaign is still active and that it represents a severe risk for users of an increasingly popular application in the context of working from home.
About the executable attachment, the researchers mention that this is a Trojan that aims to install malware payloads for later stages of attack. Once installed on the compromised system, the Trojan will install DLL files and create their administration links.
When you click on the file, it starts downloading and installing itself as a Windows program.
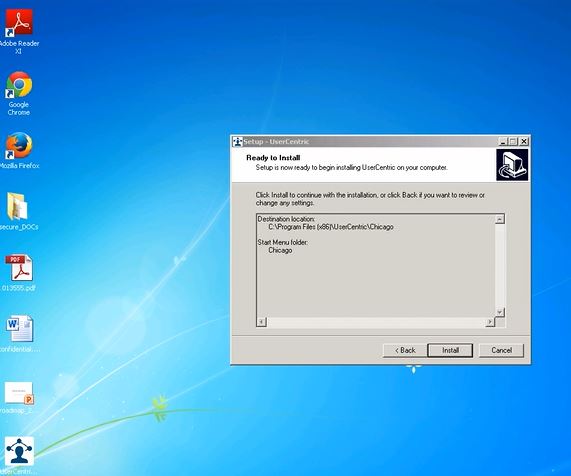
A further analysis of this file .exe by Check Point, confirms that this is a malicious payload.
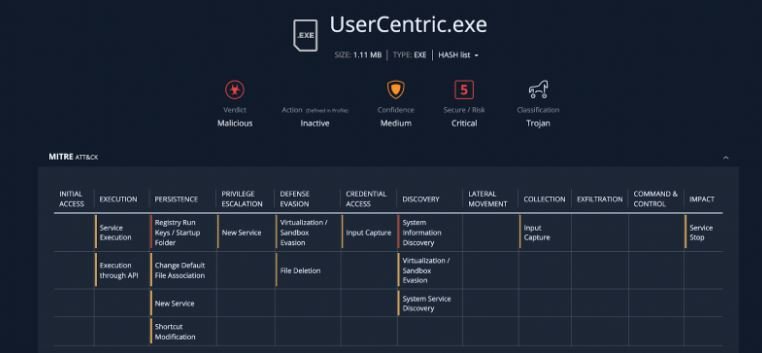
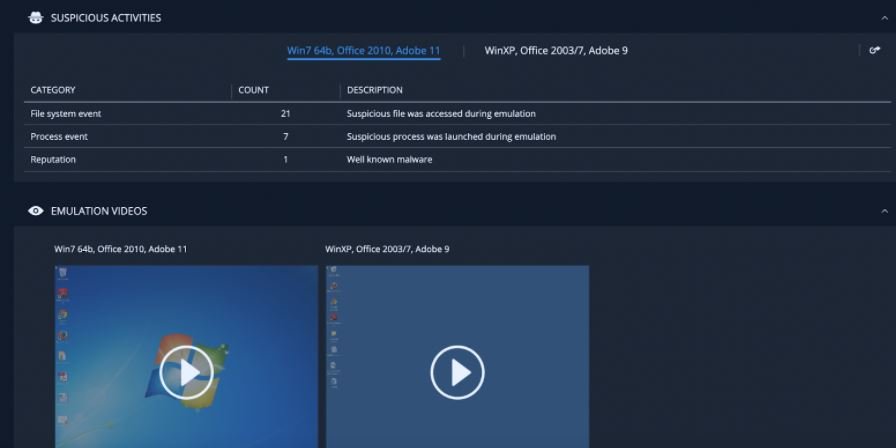
By attaching malicious files to Microsoft Teams conversations, hackers found a new method to easily compromise millions of users on this platform. In addition, gaining access to Teams platforms can be trivial for threat actors, as sometimes only one email address is required. Threat actors can steal Microsoft 365 credentials through previous phishing campaigns, gaining unrestricted access to Teams accounts and the rest of the Office suite in an affected organization.
As if that were not enough, it has been shown that some hacking groups have specialized in the compromise of this information, using traditional methods of social engineering and phishing, so this is still one of the main variants of hacking.
To protect yourself from this and other variants of hacking through platforms such as Teams, specialists recommend:
- Run downloaded files in secure environments
- Implementation of complementary security measures
- Train members of the organization to detect potential security threats
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
