Security threats for Android device users keep popping up constantly. An example of the most recent security risks detected is Xenomorph, a threat detected by researchers at the security firm ThreatFabric, who consider it a critical problem.
Xenomorph is described as a classic banking Trojan that, by infecting an Android device, requests access to the Accessibility service and abuses this tool to display fake login screens when the affected user opens a legitimate banking application. The malware collects this information, along with other data from the device, and sends it to a C&C server controlled by the hackers.
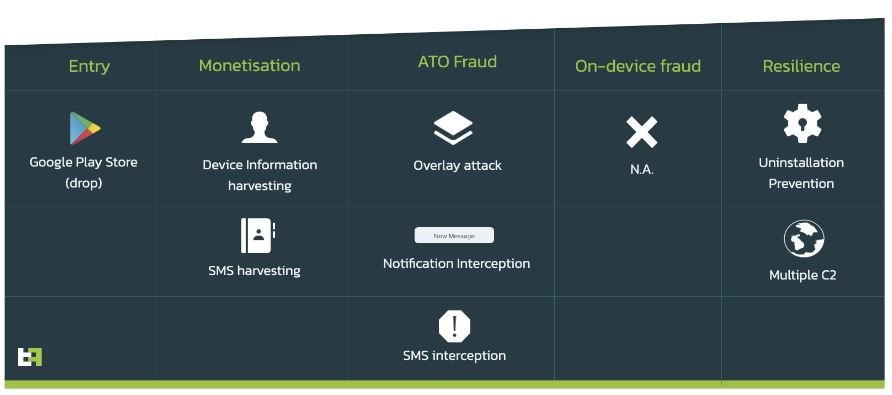
After data collection, threat actors access the accounts of affected users to empty them, even if they are protected with multi-factor authentication, as the malware is also capable of intercepting authentication SMS messages.
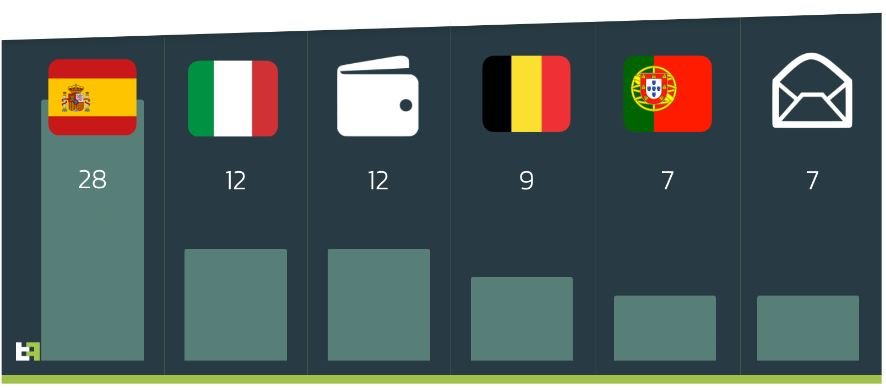
Malware samples collected by the researchers indicate that Xenomorph can display up to 56 login screens for banks in Belgium, Spain, Italy and Portugal, in addition to having fake screens from 20 cryptocurrency exchange platforms and email services.
Another characteristic feature of this Trojan is its distribution method. While other similar malware variants use malicious apps or unsafe websites for their spread, Xenomorph is hidden in some apps available on the official Google Play Store platform.
When using applications available in official repositories, threat actors employ a malware variant known as dropper, which allows them to evade security controls in the Play Store and other stores to later download a more aggressive malware variant, in this case the Xenomorph Trojan. So far only the presence of the Trojan has been detected in Fast Cleaner, an application that was downloaded by more than 50,000 users before Google removed it from its store.
Although Xenomorph is a variant of malware in development, experts fear that the threat could grow excessively, as it has already been proven that the operators of this campaign were able to evade Google’s security measures, with the potential risk of a massive attack.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
