Cybersecurity specialists report that, for some years now, a hacker has been running malicious servers throughout the Tor network in what appears to be an attempt to deanonymize users of this network. Identified as KAX17, the hacker (or group of hackers) has gone so far as to run up to 900 malicious Tor servers.
As some users may know, these servers encrypt and anonymize user traffic as it traverses the Tor network, functioning as a huge proxy environment that handles connections and loses the actual source of user traffic. These servers must have contact information, such as email addresses and other details.
Although this is a requirement of the Tor network, servers without contact information are sometimes connected, and because the network is not strictly monitored, it is not possible to guarantee that servers are always being used properly to bounce and hide user traffic.
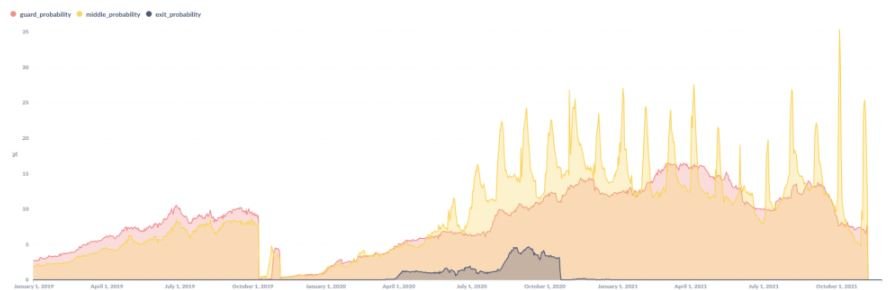
Nusenu, a Tor node operator, was the first to detect an unusual pattern related to nodes without contact information, which first occurred in 2017. Nusenu mentions that the hacker behind this campaign has been adding servers without contact information in bulk, operating servers at random points with great ease.
The expert mentioned that this is an unusual operation, since other malicious campaigns related to the Tor network focus on the operation of output relays, while KAX17 remains in the middle points of the network. The use of intermediate relays seemed to be an indication that this was a persistent operation focused on the collection of information about users on the network, which under normal conditions remains anonymous.
After detecting the malicious activity, Nusenu submitted a report to the Tor Project, so hundreds of malicious relays were removed in October 2020. Shortly thereafter the expert detected a new set of relays potentially linked to KAX17, although this has not been fully demonstrated.
Finally, a Spokesperson for the Tor Project confirmed the veracity of Nusenu’s investigation, in addition to mentioning that they will continue to monitor the detection and removal of these malicious relays, although it did not add more details about the person responsible for the malicious campaign and its real scope.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
