Cybersecurity specialists report that a malware variant for the theft of passwords, credit cards, and cryptocurrency addresses is being distributed on the Internet through an alleged pirated copy of the CCleaner optimization program.
Identified as FakeCrack, this malicious campaign was discovered by Avast experts, who mention that per day, at least 10,000 infection attempts accumulate, mainly in Brazil, France, India, and Indonesia.
This method of distribution is possible thanks to the technique known as Black Hat SEO, in which malware distribution websites are ranked in the first results of Google Search to trick as many people as possible and make them download malicious executables.
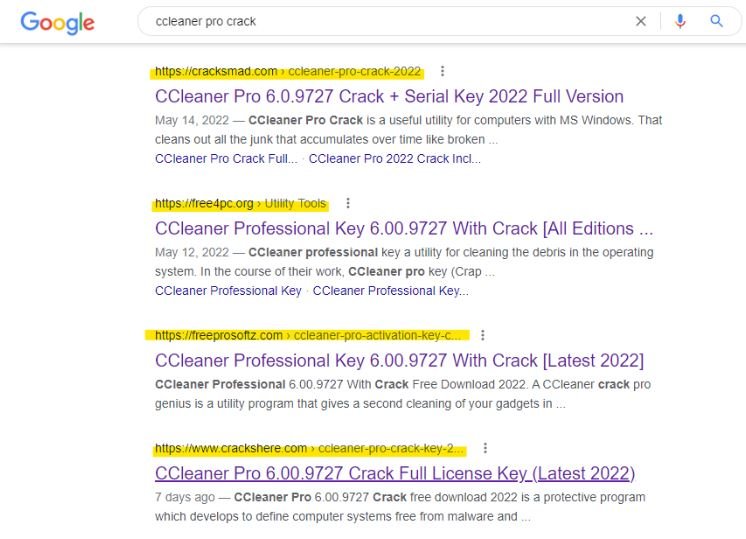
As mentioned at the beginning, the operators of this campaign attract unsuspecting users using a supposed decrypted version of CCleaner Professional, the full version of the Windows cleaner and optimizer used by millions of users in the world.
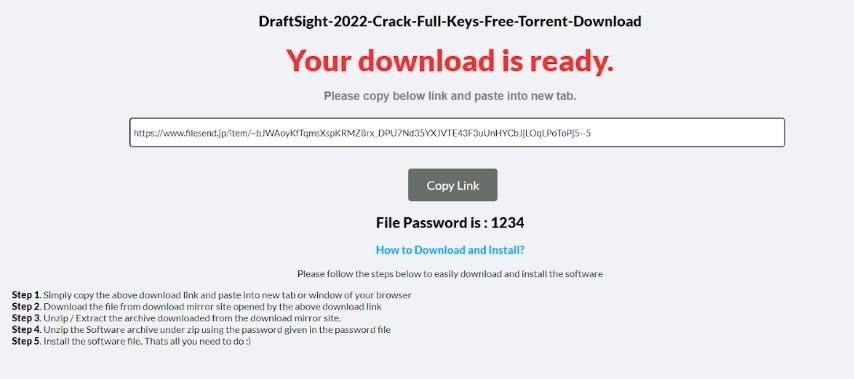
The black hat SEO allowed to position pages created by hackers among the most prominent results in search engines, getting victims to take to various platforms where the download of CCleaner was offered in the form of a ZIP file. These files were hosted on legitimate platforms and recognizable to almost anyone, such as Mediafire or Filesend.
This file is protected with weak passwords such as “1234”, a tactic with which malware operators seek to evade antivirus detection on affected systems. Researchers have identified at least eight executable file names, although the most common appears to be “setup.exe” and “cracksetup.exe.”
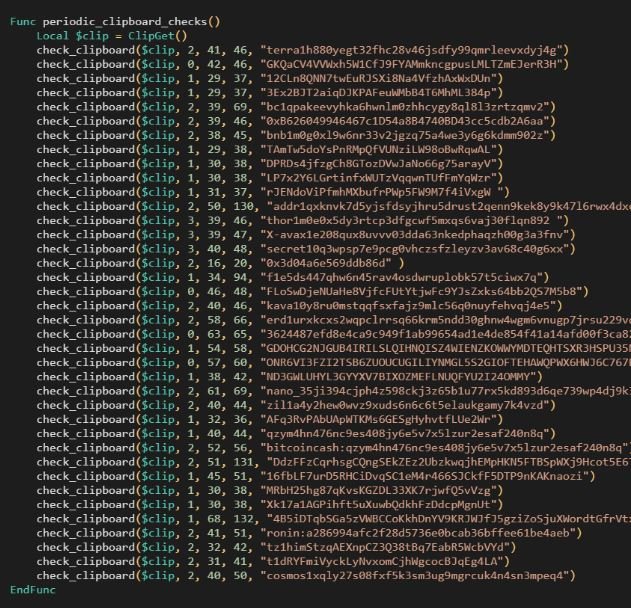
If the victims execute the downloaded file, a process of stealing sensitive information stored in web browsers, including access credentials, payment card data, and cryptocurrency addresses will be initiated. This malware can also monitor the system clipboard to, in case of detecting a copied cryptocurrency address, replace legitimate information with an address under the control of hackers and thus divert virtual assets.
Finally, malware can use proxies to steal credentials associated with cryptocurrency exchange platforms through a Man-in-The-Middle (MiTM) attack, a hacking variant that is very difficult for affected users to detect.
As in any similar case, the main recommendation is not to download pirated software from unknown sources, as this remains one of the main tactics for the distribution of all kinds of malware variants.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
