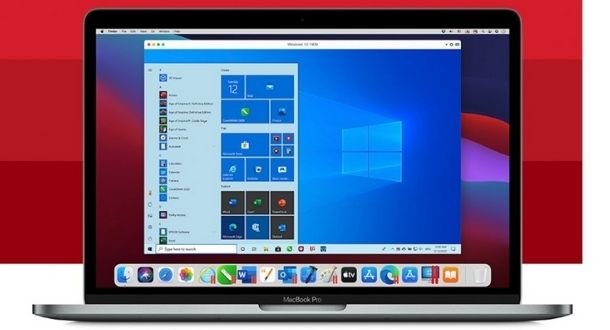
Free tool to detect Log4j components in your network infrastructure: Check if your servers are vulnerable
Exploiting vulnerabilities detected in previous versions of Log4j remains a severe issue, so the cybersecurity community is still looking for the best ways to prevent a cyberattack. However, some usersRead More →